Another day, another trove of sensitive data exposed online. This time, a MongoDB database containing a whopping 43.5GB of the dataset used in marketing campaigns has been left exposed for public access.
The data was discovered by Bob Diachenko, an independent security researcher who noted that the database was available on an unprotected MongoDB hosted on Grupo-SMS hosting and indexed on Shodan on September 13th.
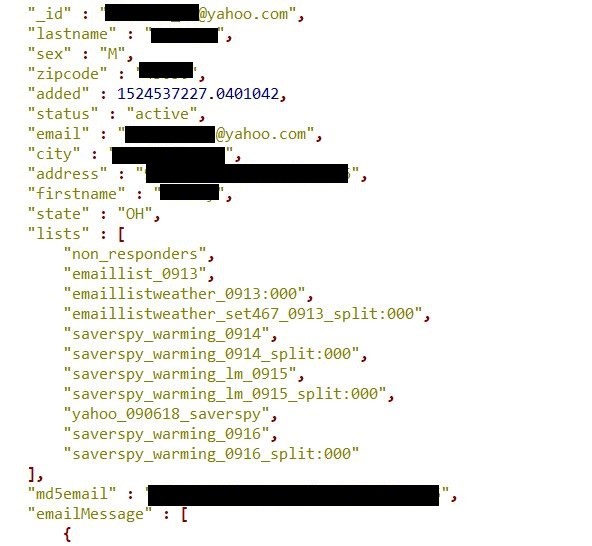
According to Diachenko’s analysis, the 43.5GB of dataset contained 10,999,535 (almost 11 million) Yahoo-based email addresses, personal details like names, gender, physical addresses including city, state and zip code. Furthermore, DNS records related to email status (sent or received) were also part of the database.
It is unclear who uploaded the data on unprotected MongoDB, however, since the data was titled “Yahoo_090618_ SaverSpy” Diachenko believes that there is a direct connection between SaverSpy, a daily deals website operated by Coupons.com.
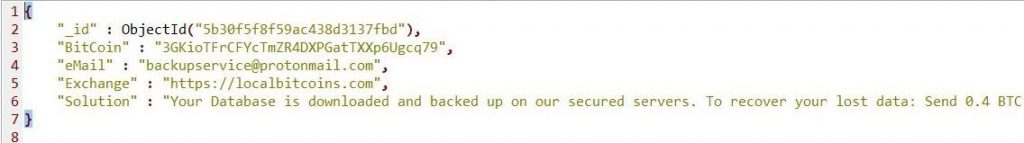
Both platforms were contacted by the researcher however at the time of publishing this article; there was no response from either of them. It is noteworthy that Shodan had already tagged the unprotected MongoDB as “compromised” and it also contained ‘Warning’ database with ‘Readme’ collection and ransom note demanding 0.4 Bitcoin for recovering the data.
“At the time of discovery, all data were intact. I assume this is a result of failed script scenario used by crooks (and pure luck for the database owners),” said Diachenko.
This is not the first time when an unprotected MongoDB has been exposed online. In fact, MongoDB has a history of being targeted by hackers for ransom and putting user data at risk; for instance in 2016, in two separate incidents, hackers leaked 58 million accounts belonging to a leading business firm while in another attack 36 million MongoDB accounts were exposed online for public access.
In January last year, several MongoDB databases were targeted by cyber-criminals for ransom. The same year, unprotected MongoDB exposed medical data of veterans affected by sleep disorders. The evolved version of MongoDB ransomware was also found targeting MySQL databases.
The sensitivity of the matter can be assessed by a test carried out by Diachenko and his team in which they left a honeypot MongoDB database containing 30GB of fake data. Little did they know, it took only three hours for hackers to identify the database before wiping out its data in just 13 seconds and leaving a ransom note demanding 0.2 Bitcoin.