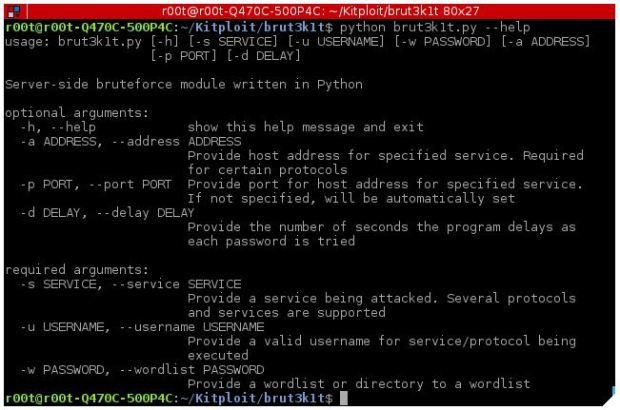
As an introduction, brut3k1t is a bruteforce module on the server side that supports dictionary attacks for various protocols, information security experts say.

Some of the current protocols that are complete and compatible are:
- ssh
- ftp
- smtp
- XMPP
There will also be implementations of different protocols and services including Twitter, Facebook and Instagram.
The professionals tell us, that the installation is very simple. brut3k1t requires several dependencies, the program will install them if you do not have them.
- argparse – used to analyze command line arguments
- paramiko: used to work with SSH connections and authentication
- ftplib: used to work with FTP connections and authentication
- smtplib: used to work with SMTP connections (email) and authentication
- fbchat – used to connect with Facebook
- selenium: used to scrape the network, which is used with Instagram (and later with Twitter)
- xmppy – utiized for XMPP connections .
The download is simple. git clone https://github.com/ex0dus-0x/brut3k1t
Change to directory:
cd /path/to/brut3k1t
We will talk about the use. Using brut3k1t is more complicated than just running a Python file, say information security professionals. By typing python brut3k1t -h it shows the help menu.

The researchers give us some examples of its use, cracking the SSH server running on 192.168.1.3 using root and wordlist.txt as a list of words.
python brut3k1t.py -s ssh -a 192.168.1.3 -u root -w wordlist.txt
The port will be automatically set to 22, if it is different, specify with -p indicator.
Cracking email [email protected] with wordlist.txt on port 25 with a delay of 3 seconds. For email, experts say that the SMTP server address should be used. As an example, Gmail = smtp.gmail.com. You can investigate this with Google.
python brut3k1t.py -s smtp -a smtp.gmail.com -u [email protected] -w word list.txt -p 25 -d 3
Cracking XMPP [email protected] with wordlist.txt on port 5222. XMPP is similar to SMTP, you must provide the XMPP server address, creep.im.
python brut3k1t.py -s xmpp -a creep.im -u test -w wordlist.txt
Cracking Facebook is more complicated, it will require the target user ID, not the username.
python brut3k1t.py -s facebook -u 1234567890 -w wordlist.txt
Instagram cracking with username test with wordlist.txt and 5 seconds delay
python brut3k1t.py -s instagram -u test -w wordlist.txt -d 5
Here we will leave some notes to take into account. Use this article for educational purposes, as well as for the learning code and safety-oriented practices.
In the case where the port indicator -p is not provided, the default port for that service will be used. It is not necessary to provide it for Facebook and Instagram, says the information security researcher.
In the absence of the delay indicator -d, the default delay in seconds will be 1.
Experts say to use the SMTP server address and the XMPP server address for the address -a, for SMTP and XMPP, respectively.
Some protocols are not based on the default port. An FTP server may not be on port 21.