The security researchers at ESET have uncovered InvisiMole: a spyware that has been active at least since 2013. The company’s security products recently detected it in Russia and Ukraine.
As its name suggests, InvisiMole remains hidden and performs highly targeted actions with low infection ratio. The malicious components of the malware turn the computer into a spying video camera to closely monitor the victim’s activities.
Its capabilities also include inspecting the PC for system information, running services, active processes, networking information, scanning wireless networks, tracking geolocation, monitoring specific drives, etc. All these tasks are performed using component modules — RC2FM and RC2CL.
The working of this spyware can be explained using its modular architecture. The very first module is a wrapper DLL that makes the malware look like legitimate DLL file. The malware can be launched by hijacking a DLL and loading the wrapper module during the Windows startup process instead of the legitimate DLL.
Apart from hijacking, the malware also employs other loading and persistence methods, including the installation of a registry key and scheduling a task.
No matter what persistence method this spyware adopts, the actual attack payload remains the same. Finally, after connecting to its command & control server, additional data is downloaded to perform the backdoor actions.
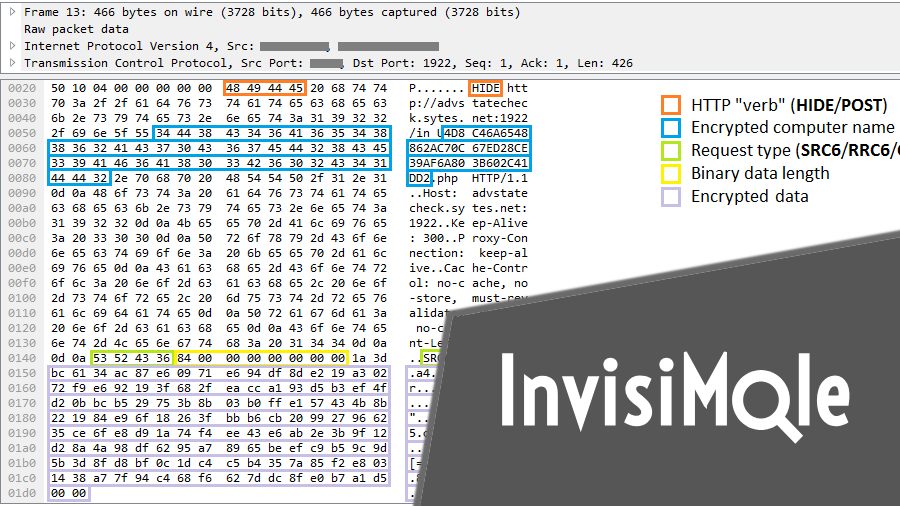
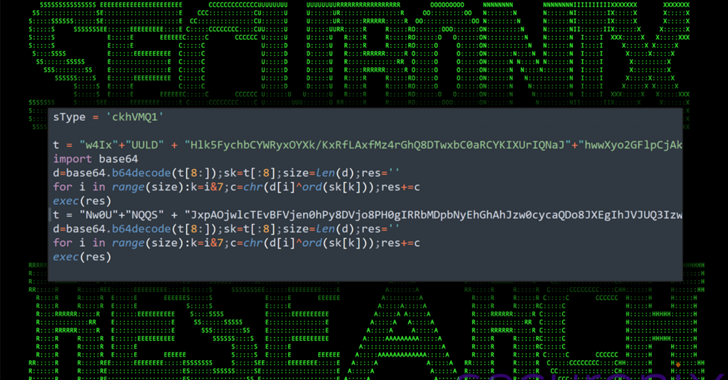
InvisiMole encrypts its internal files, strings, network communication, and configuration data to remain hidden.
You can read the complete technical analysis of InvisiMole spyware on ESET’s blog and get to know more about this notorious hacking tool.