Cybersecurity specialists report the discovery of a remote code execution (CER) vulnerability in the Steel-Belted Radius (SBR) Carrier Edition, a device developed by Juniper Networks and used by telecommunications operators for the management of network access and security policies.
Tracked as CVE-2021-0276, the vulnerability resides in SBR Carrier versions 8.4.1, 8.5.0, and 8.6.0 that use the Extensible Authentication Protocol. The company issued a security patch on Wednesday, noting that the flaw received a score of 9.8/10 according to the Common Vulnerability Scoring System (CVSS).
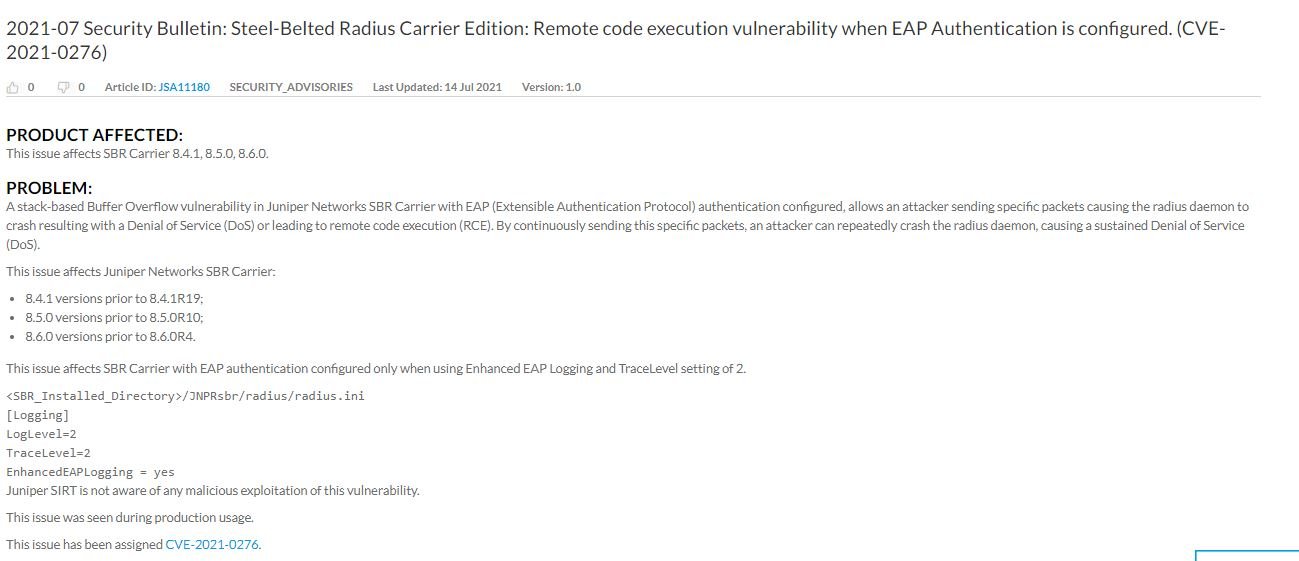
The flaw was described as a stack-based buffer overflow error that threat actors can exploit by sending specially crafted packets to the affected platform, forcing the RADIUS daemon to crash. A successful attack would trigger the RCE condition and even in a denial of service (DoS) scenario.
In addition to this flaw, Juniper Networks security teams fixed a large number of bugs, releasing updates to their product lines, including some bugs that would trigger DoS conditions. Another prominent flaw is CVE-2021-0277, which was described as an out-of-bounds read vulnerability and which received a CVSS score of 8.8/10. The flaw lies in multiple versions of the Junos OS and Junos OS Evolved operating system.
This flaw lies in the processing of specially crafted LLDP frames by the Layer 2 Control Protocol (l2cpd) daemon. LLDP is the protocol that network devices use to transmit their identity, capabilities, and neighbors on a local area network.
In case you can’t upgrade to a secure version, Juniper Networks points out that there are some mitigation measures. For example, users can configure a device not to load the l2cpd daemon. However, if it is disabled, certain protocols will not work. A second option is to configure target interfaces on the device to disable the processing of LLDP.O packets.
An additional option is to configure interfaces on the device to disable the processing of LLDP packets. Or, for most switching platforms, it is possible to implement packet filters through a firewall to discard LLDP packets with an EtherType of 0x88cc.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















