Many of the most sophisticated malware variants have the ability to analyze whether the system on which they run is protected by a sandbox; if so, these malware variants can disable their functions and hide from security systems.
Although implementing a sandbox is one of the critical parts for malware analysis, it is not always possible to perform such implementations, so it is necessary to think of other alternatives to prevent these infections. This time, experts from the International Institute of Cyber Security (IICS) will show you how to implement fake backdoor processes, which will scare any threat actor away trying to meddle in their systems.
Needless to say, a fake sandbox does not guarantee protection against malware, although malware analysis experts claim that many of the most popular security threats (Petya, Bad Rabbit, among others) base their operation on detecting a sandbox.
In this process we will need the fake-sandbox utility, which contains a PowerShell script and the corresponding installation files.
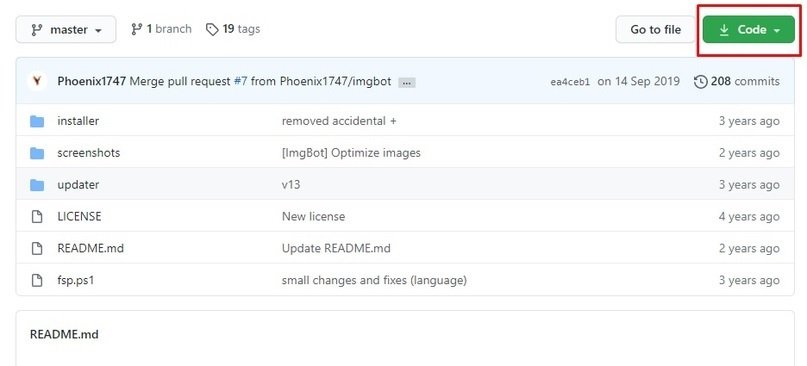
Let’s start with the initial screen. Download the entire file from the specified repository and unzip it to the required directory. Malware analysis experts point out that the required script is fsp.ps1, which must be run using PowerShell or cmd.exe by entering the command with the utility:
Powershell -executionpolicy remotesigned -F 'Your Path fsp.ps1'
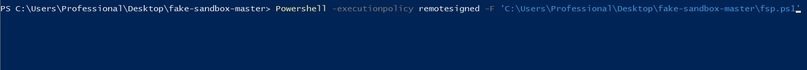
Whichever method you choose, the result should be something like this:
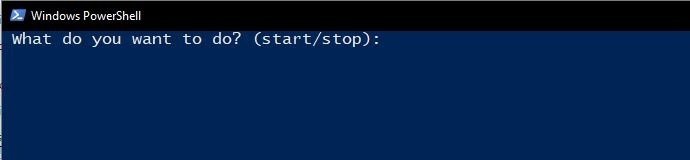
Now we can start the available impersonation processes by typing “start” or “stop” respectively, to delete them. The script will instantly start all processes and the result should look as shown below:
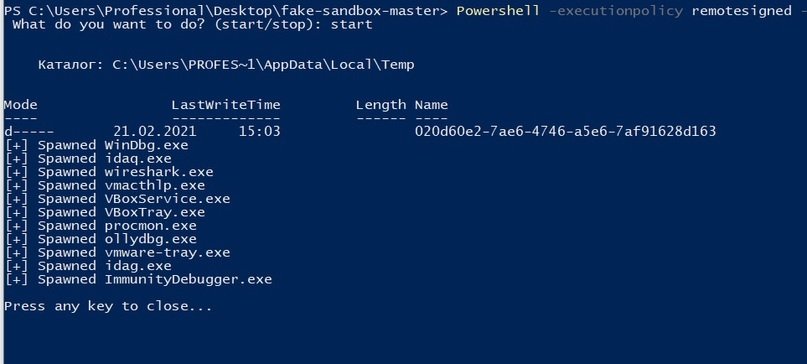
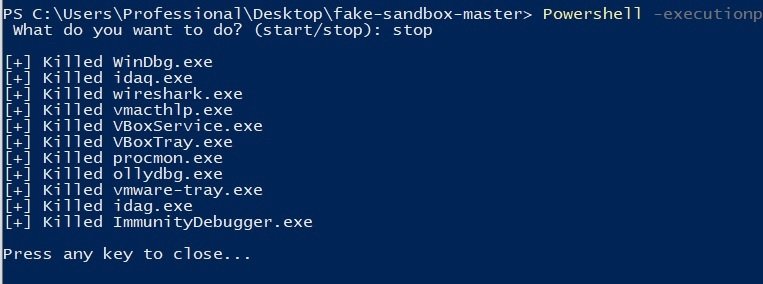
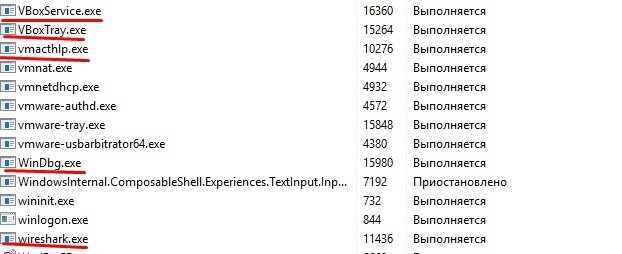
If after that we open the task manager, we will see several newly launched command line processes. If you use programs such as the system browser, you can see that only basic tasks are performed. The processes themselves are called “WinDbg.exe”, “wirehark.exe”, etc.
On how it works, malware analysis experts point out that there is a section containing fake process names, and we can add our processes to the $fakeProcesses. The script will then copy ping.exe to a temporary directory and rename these copies to the given process names. For this to work while the PC is powered on, the script will ping the invalid IP address 1.1.1.1 every hour for an unlimited period of time. This ensures the minimum load on the system and also ensures that the processes do not disappear. The stop argument will simply kill what is specified in $fakeProcesses.
The only problem with the script is that it is not persistent, so its will disappear after you log back in and you will need to restart the script. To simplify this entire solution, there is an installer that automatically places all the files in the %AppData%-Roaming-FakeSandboxProcesses directory and a small pack of triggers. To do this, run the fsp-installer file.bat in the installer section, the malware analysis experts point out.
No administrator rights are required, so you only need to run the batch file in the command line window and enter “i” to start the installation, then enter “y” if you also need to install the auto-update component or “n” if you don’t need it to install it. Then we press any button to close the command line window and the installation will be complete. Processes will now start automatically when the computer is turned on.
It is important to note that malware analysis experts recommend whitelisting the batch file for antivirus software to run automatically in the FakeSandboxProcesses folder and appData directory. Otherwise, the antivirus can identify it as malware and prevent it from spreading. Kaspersky detects the batch file as a Trojan:
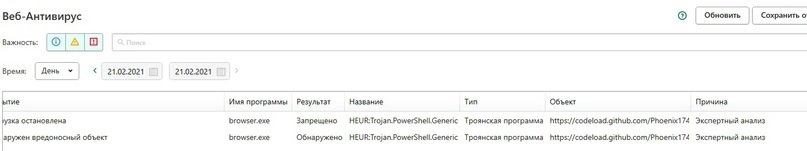
Obviously, this script is not a Trojan. In short, fake sandbox processes are an easy way to make malware believe it is being scanned, which can function as a first layer of security on any system.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.