Security teams at telecommunications firm T-Mobile are investigating a data breach after a hacker appeared claiming he has access to the records of some 100 million customers. The investigation began after the company was alerted to a dark web post offering the information for sale in exchange for 6 Bitcoin.
Although the seller does not specify in his post how he obtained this data, an investigator managed to contact him and was able to learn that the information was extracted during an incident of attack on T-Mobile’s servers.
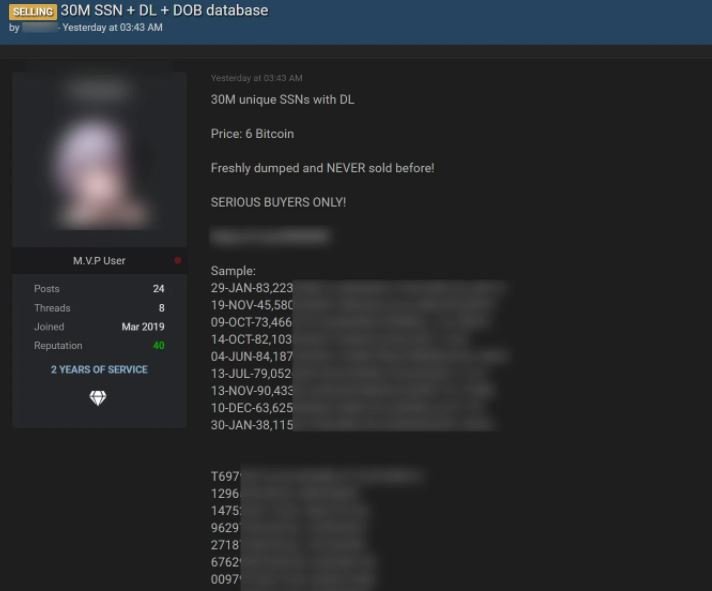
The vendor claims that the production, preparation and development servers were compromised a couple of weeks ago, plus the leak includes full names, phone numbers, dates of birth, social security numbers, IMSI and IMEI keys and other sensitive details.
The vendor shared some screenshots of an SSH connection to a compromised production server to demonstrate the legitimacy of the incident.
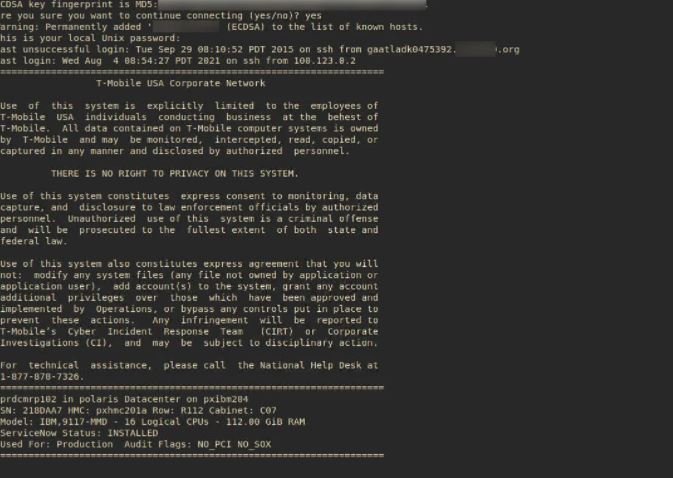
Members of the cybersecurity community have analyzed the leak and concluded that this information actually belongs to T-Mobile customers. Moreover, cybersecurity firm Cyble points out that the actors behind the attack could also have stolen some additional databases from the affected systems.
Finally, investigators at the Hudson Rock firm claim to have contacted the hacker responsible for the incident, who mentioned that the main motivation for the attack was to retaliate against the U.S. government for the kidnapping and torture of John Erin Binns. This man is a resident of Turkey who decided to sue the Federal Bureau of Investigation (FBI) and the Central Intelligence Agency (CIA) accusing agents of both organizations of torturing him with political motivations. “The main intention is to harm the U.S. government,” the hackers claimed.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















