Dero is a relatively new cryptocurrency that places a strong emphasis on privacy. It utilizes directed acyclic graph (DAG) technology, which allows it to make the claim that its transactions are completely anonymous. The combination of anonymity and a greater rewards ratio makes it potentially attractive for cryptojacking organizations in comparison to Monero, which is the coin that is most often used by attackers or groups conducting miner operations. CrowdStrike has discovered the first-ever Dero cryptojacking operation targeting Kubernetes infrastructure.
A cryptojacking operation using Monero was also discovered; this operation is aware of the Dero effort and is actively competing with it. The Monero campaign mines XMR on the host by elevating their privileges via the usage of DaemonSets and mounting the host as the root user.
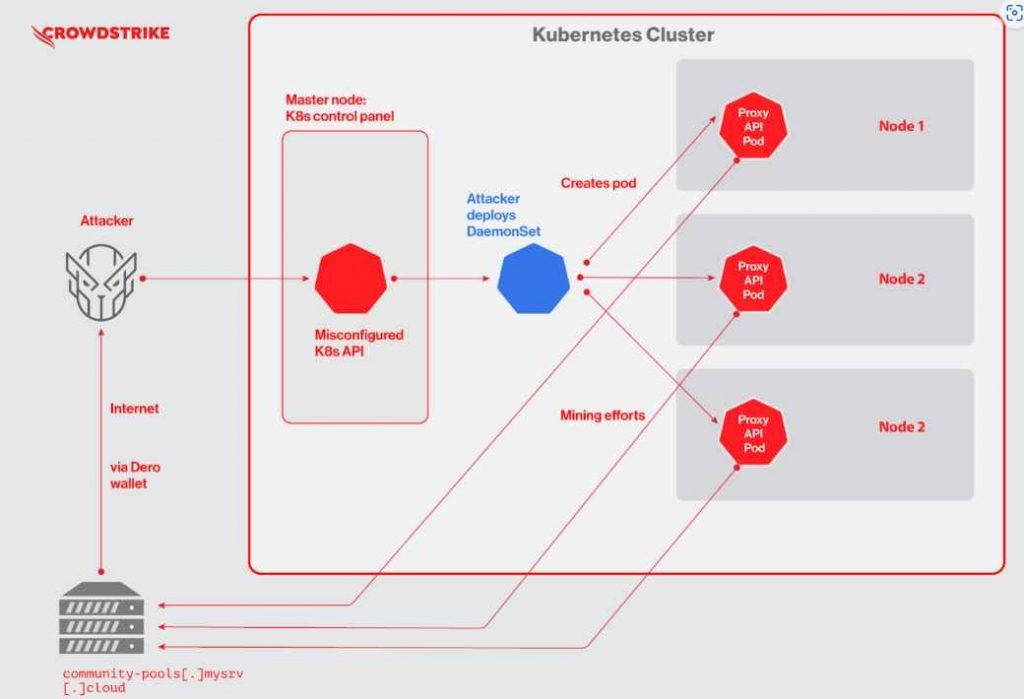
Attackers specifically targeted Kubernetes clusters running on non-standard ports by scanning for and locating exposed vulnerable Kubernetes clusters that had the authentication setting —anonymous-auth=true. This setting enables anonymous access to the Kubernetes API and was the target of the attackers’ attention. It is possible for a user with adequate access to mistakenly expose a secure Kubernetes API on the host where kubectl is operating by performing the “Kubectl proxy” command. This is a less apparent approach to expose the secure Kubernetes cluster without authentication. The Kubernetes control plane application programming interface does not provide anonymous access out of the box in Kubernetes. Nevertheless, since the choice to make secure-by-default the default was delayed, and there are a variety of ways in which Kubernetes might be inadvertently exposed, there is still a legacy of exposed systems on the internet.
After the first engagement with the Kubernetes API, the attacker will next install a Kubernetes DaemonSet with the name “proxy-api.” On every node in the Kubernetes cluster, the DaemonSet installs a pod that contains malicious code. This makes it easier for attackers to operate a cryptojacking operation by simultaneously using the resources of all of the nodes in the network. The mining efforts that are performed by the pods are donated back to a community pool. This pool then divides the reward (in the form of Dero currency) among all of its contributors in an equitable manner via their own digital wallets.
Once the vulnerable Kubernetes cluster had been compromised, the attackers did not make any attempts to pivot either by moving laterally to attack additional resources or by scanning the internet for discovery. This is a pattern that is common among many cryptojacking campaigns that have been observed in the wild.
In addition, the attackers did not try to remove or interfere with the functioning of the cluster. Instead, they used a DaemonSet to mine Dero. The name of the DaemonSet was disguised as “proxy-api,” and the name of the miner was “pause,” both of which are phrases that are often seen in Kubernetes logs.
These targeted behaviors seem to define the goal of this campaign, which is that the attackers are only seeking to mine for Dero. This is the conclusion that can be drawn from the actions that have been taken. As a result, we have reason to believe that a cryptojacking actor driven by financial gain is the one responsible for this initiative.
Attackers have taken advantage of the fact that Kubernetes has become the most popular container orchestrator in the world to focus their attention on misconfigurations, design flaws, and zero-day vulnerabilities inside Kubernetes and Docker.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.