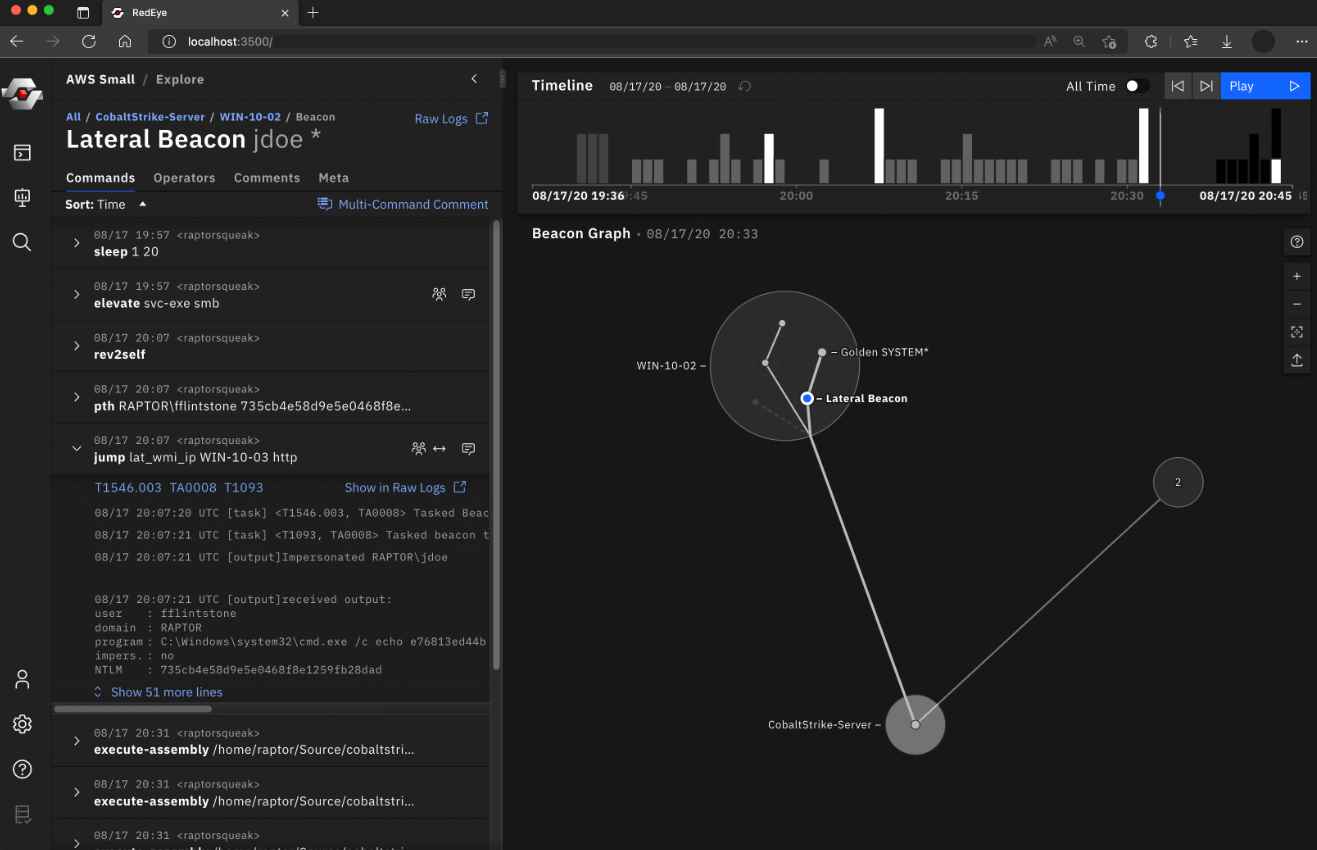
Researchers from multiple security companies have reported that a massive supply chain attack on users of 3CX, a widely utilized voice and video calling desktop client, was carried out by computer hackers working on behalf of the government of North Korea. The attack targeted users of the Windows and macOS operating systems. 3CX users may make calls, examine the status of colleagues, chat, plan a video conference, and check voicemails all from the desktop program by using the 3CXDesktopApp, which is accessible for Windows, macOS, Linux, and mobile devices.

The attack resulted in the compromising of the software build system that was used to generate and distribute versions of the app for Windows and macOS. The app delivers VoIP and PBX services to “over 600,000 clients,” some of which include American Express, Mercedes-Benz, and Price Waterhouse Cooper. Since the attackers controlled the software development system, they were able to insert malware into 3CX applications, even though those applications had been digitally signed using the official signing key for the firm.
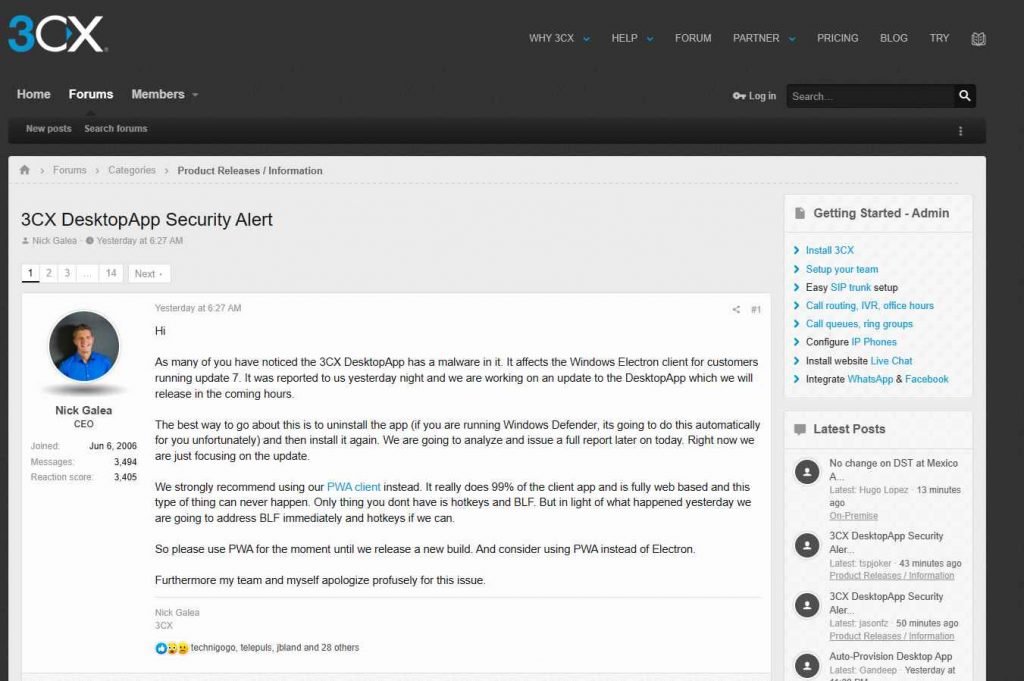
This is a traditional kind of attack on supply chains, and its purpose is to take advantage of the trust connections that exist between an organization and third parties.
According to the cybersecurity company CrowdStrike, the infrastructure and encryption key used in the attack are identical to those seen in a campaign carried out by Labyrinth Chollima on March 7. Labyrinth Chollima is the tracking name for a threat actor that is aligned with the North Korean government.
The attack was first discovered late on Wednesday night, when products from a variety of different security organizations started identifying malicious activity emanating from properly signed binaries for 3CX desktop applications. No later than February 2022, the threat actor registered a huge collection of domains that were used to interact with infected devices. These domains were employed in the preparations for the complex operation that was to follow. Around the 22nd of March, the cybersecurity company Sentinel One saw an increase in the number of behavioral detections of the 3CXDesktopApp. On the same day, 3CX customers began online discussions about what they thought could have been erroneous 3CXDesktopApp detections by their endpoint security programs.
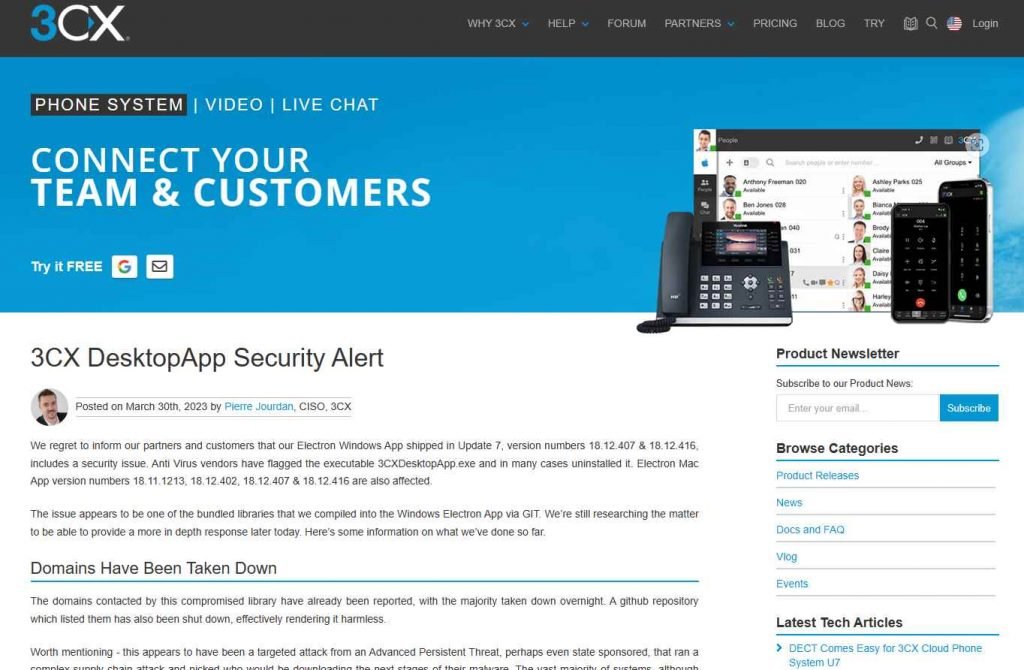
Electron Mac App versions 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 all include a “security problem,” according to 3CX Chief Information Security Officer Pierre Jourdan. He claimed the payloads were put into packaged libraries produced using Git, a mechanism that software developers use to monitor changes in the programs they create. According to him, a significant number of the servers owned by the attackers that compromised workstations attempt to communicate with have already been taken down.
Since the 2020 attack on SolarWinds, which resulted in data breaches at businesses and governmental organizations all across the globe, software vendors have been on high alert for supply-chain invasions.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.