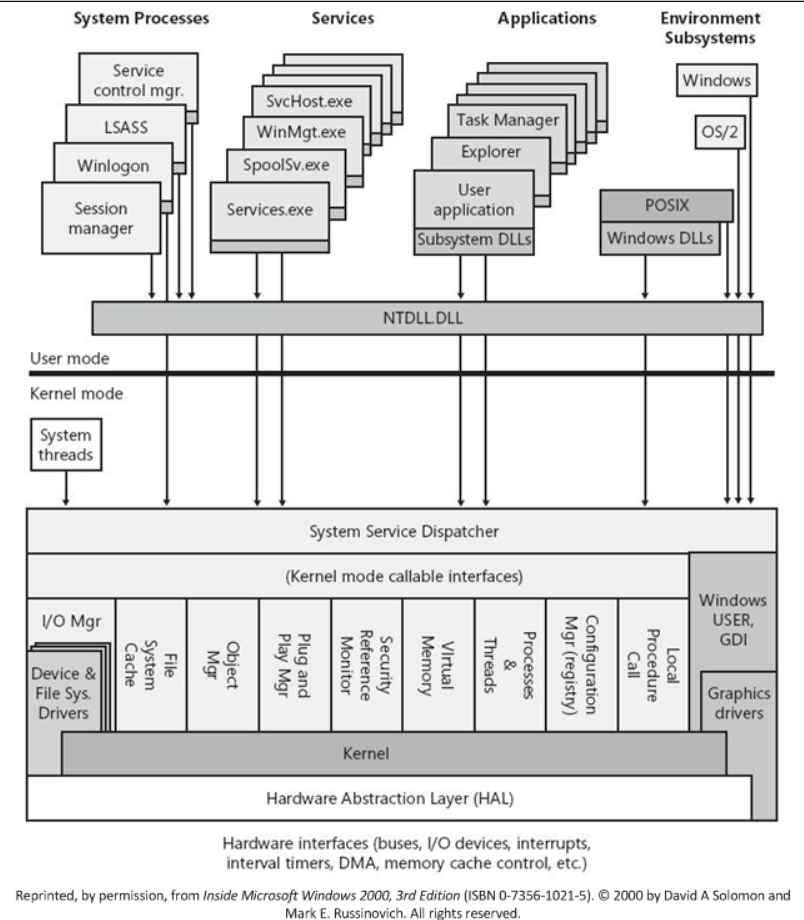
This cybersecurity information sheet (CSI) is being released by the National Security Agency (NSA) in collaboration with the Cybersecurity and Infrastructure Security Agency (CISA). The purpose of this document is to provide recommendations and best practices for improving defenses in cloud implementations of development, security, and operations (DevSecOps). This CSI explains how to integrate security best practices into typical software development and operations (DevOps) Continuous Integration/Continuous Delivery (CI/CD) environments, without regard for the specific tools being adapted, and leverages several forms of government guidance to collect and present proper security and privacy controls to harden Continuous Integration/Continuous Delivery cloud deployments. Software supply chains and continuous integration and deployment (CI/CD) systems are appealing targets for malicious cyber actors (MCAs), as indicated by a rising number of intrusions over time.When securing a CI/CD environment, it is essential to be aware of the many security risks that might have an effect on the operations and to take precautions to safeguard against each of these risks individually.As seen by the steadily increasing number of incursions over the course of time, the continuous integration and continuous delivery (CI/CD) systems as well as software supply chains are prominent targets for cybercriminals.
The Continuous Integration and Continuous Delivery (CI/CD) development methodology enables businesses to dynamically merge code changes while simultaneously preserving the integrity of their application code base. It expedites the process of constructing and testing modifications to the code.The Continuous Integration and Continuous Delivery (CI/CD) paradigm is an essential part of the (DevSecOps) concept, which integrates security and automation into all stages of the software development lifecycle.
Commercial cloud environments are a common location for the deployment of continuous integration and continuous delivery pipelines due to the significance of the cloud in relation to IT modernization activities.
Recommendations To Secure CI/CD Environments
Make use of the cryptography recommended by the NSA.
The National Security Agency (NSA) and the Computer Security Industry Association (CISA) both recommend adopting robust cryptographic algorithms and configurations when developing cloud-based applications and services. The correct implementation and configuration of these strategies results in an increase in the level of security afforded to any information, trade secrets, application programming interfaces (APIs), and keys that are generated across the CI/CD pipeline.
Reduce as much as possible your reliance on lengthy credentials
Employ robust credentials wherever doing so is feasible. These credentials should be able to withstand attempts to steal, phish, guess, and replay them. When human authentication is necessary for SSH or other keys, using identity federation and security tokens that are resistant to phishing attacks are the best ways to get them.
Incorporate a signature into the CI/CD setup, and then verify it
The National Security Agency and the Computer Security Industry Association both recommend using secure code signing in order to build digital trust inside the CI/CD pipeline. Make sure that the code is signed in a consistent and accurate manner, and that the signature is verified, no matter what degree of development the project is at. If the signature cannot be verified for whatever reason, investigate the possible reasons behind this. It might be a problem with the default settings, or it could be a sign of a more serious violation.
Implement the two-person rule, sometimes known as the 2PR, for all code modifications
It is best practice to prohibit a single developer from checking in code without first obtaining another developer’s feedback and authorization. This method not only enhances the quality of the code in general, but it also makes it far less probable that malicious code will be successfully checked in even if the credentials of a single developer are stolen.
Establish rules for CI/CD access based on the principle of least privilege
It is not appropriate for all employees of the firm to have access to the CI/CD pipeline. Rather than being given access to all pipelines automatically, employees should only be offered limited access with specified credentials upon request rather to having access to all pipelines automatically granted. Developers should only have access to the pipelines and components that are being changed by their work. In addition, multi-factor authentication (MFA), which may lessen the risks associated with using passwords, should be implemented.
Ensure the safety of user accounts
Regular audits of administrative user accounts should be performed, and access should be restricted following the principles of least privilege and separation of tasks. records should be audited to ensure that new accounts are legitimate.
Secure secrets
It is very necessary to securely manage secrets, tokens, and other credentials while working with a CI/CD pipeline. Sending sensitive information via a pipeline in unencrypted should never be done. Be sure that no sensitive data, such as passwords and secret keys, is ever stored in software that may be reverse-engineered. This includes taking all necessary precautions to prevent such data from being exposed.
Establish network subdivisions and filter incoming and outgoing traffic
Implementing and strictly enforcing an effective network segmentation strategy across all networks and services is essential for preventing the spread of malware and limiting access from other parts of the network to which users do not need access. It is strongly suggested that a demilitarized zone be set up in order to put a halt to unregulated network connection. The traffic on the network should be filtered such that communications from known malicious IP addresses cannot enter or exit the network.
Resiliency may be planned for, built, and tested
Construct the pipeline to have a high level of availability, and perform regular drills to simulate a catastrophe. During the process of threat modeling for the pipeline, it is important to take into account risks to its availability in addition to those to its confidentiality and integrity.
It was essential to ensure that the CI/CD pipeline could elastically grow so that new artifacts could be created and deployed across all of the compute instances as rapidly as possible. This was critical in order to address the Log4Shell vulnerability that existed in a variety of scenarios. Think about include coverage for emergency patch updates in the service level agreements (SLA) that your company uses.
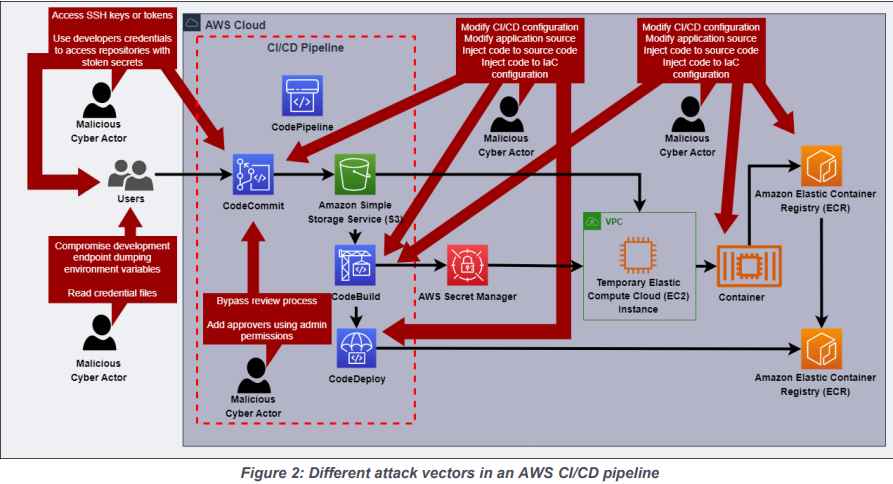
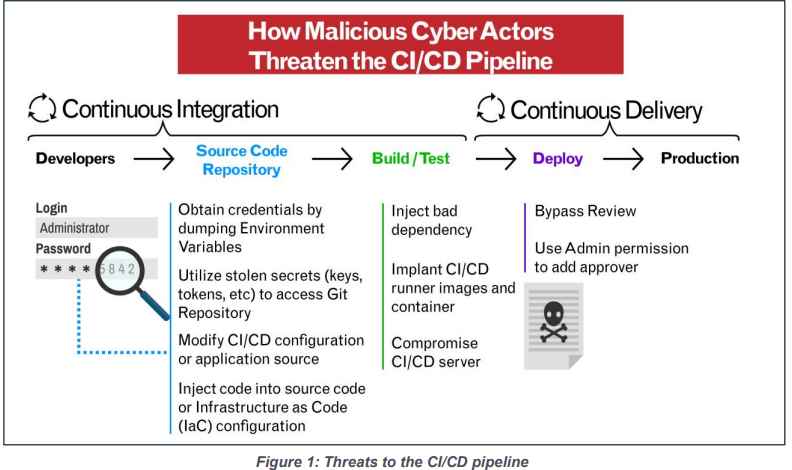
When compared to the other components of the software supply chain, the CI/CD pipeline possesses a unique and distinct attack surface of its own. By using the source software and deploying it to numerous operating contexts, MCAs have the ability to significantly magnify the affects they have. MCAs may obtain access to sensitive data and services by abusing a CI/CD environment, which allows them to build a foothold in company networks and gain admission.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.