Agent Smith malware exploits Android vulnerabilities to target unsuspected users for credential stealing.
The IT security researchers at CheckPoint have discovered a new variant of smartphone malware whose primary target is Android devices and so far the malware has infected more than 25 million Android devices.
Dubbed “Agent Smith” by researchers; the malware identifies and exploits vulnerabilities in Android OS and replaces existing apps on the targeted device with malicious ones – All that is done without permission or knowledge of the victim. It is worth noting that Agent Smith disguises as Google-related app.
Currently, Agent Smith has capabilities to steal sensitive information from Android devices such as banking credentials and private messages, etc. Furthermore, the malware works as an adware to spam users with fraudulent ads to make extra money which somehow follows the same pattern found in CopyCat, Gooligan and HummingBad attacks.
What’s worse is that the number of targeted devices is not limited to Android’s older version such as Android 5 and 6 but those on newer versions have also been infected in this campaign.
According to Check Point, the malware was initially discovered in early 2016 on “9Apps,” a third-party app store. At that time, the malware was present in Google related updaters. The researchers believe that Agent Smith’s author is working on to spread the malware infection on the Play Store. In fact, researchers notified Google about 11 malicious apps on Play Store including two Jaguar Kill Switch infected apps which were already had 10 million downloads.
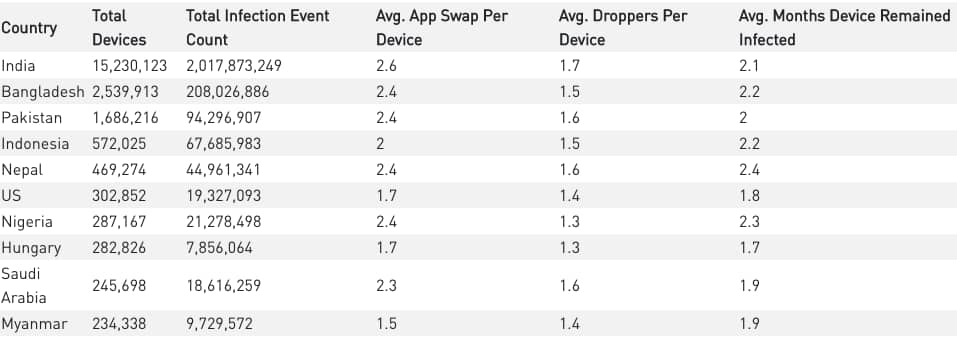
For now, most of Agent Smith’s victims are based in India however users in other Asian countries including Pakistan and Bangladesh are also among its victims. However, researchers have identified a significant number of devices infected with Agent Smith in Saudi Arabia, the United Kingdom, and the United States.
“The actors behind Agent Smith seem to have moved into the more complex world of constantly searching for new loopholes, such as Janus, Bundle, and Man-in-the-Disk, to achieve a 3-stage infection chain, in order to build a botnet of controlled devices to earn profit for the perpetrator,” said CheckPoint’s researchers in their blog post.
At the time of publishing this article; Google successfully removed all 11 infected apps from Play Store yet it raises questions on Google’s security for Android.
Moreover, researchers have highlighted the risks surrounding Android devices and adviced that businesses and users should work on “having an advanced mobile threat prevention solution installed on the device to protect themselves against the possibility of unknowingly installing malicious apps, even from trusted app stores.”
“The “Agent Smith” campaign serves as a sharp reminder that effort from system developers alone is not enough to build a secure Android eco-system. It requires attention and action from system developers, device manufacturers, app developers, and users, so that vulnerability fixes are patched, distributed, adopted and installed in time.”
Usman Rahim, Digital Security and Operations Manager for The Media Trust also commented on the growing threat of Agent Smith: “Agent Smith taps into the growing convergence of adware and malware. Bad actors are using adware to commit various forms of fraud and identity theft. One thing is for sure, app providers should carefully vet the adware vendors they work with if they want to protect their brands and their revenue.”
“As the recent GDPR fines show, being the victim of a hack can put you in regulatory trouble to the tune of hundreds of millions of dollars. In this regulatory environment, there simply is no other defense than knowing who you’re working with and what they’re doing to your users,” Usman told Hackread.
If you are an Android user, watch out for this malware threat and refrain from downloading unnecessary apps from Play Store and third-party websites. Also, use a reliable anti-virus software program and educate yourself about ongoing threats and their prevention.