Malware campaigns have become quite regular on Apple devices and as per the new report from Confiant, a cyber-security firm, there’s a new group on the block called that is specifically targeting Apple users through malvertising. The group called VeryMal has employed steganography technique this time to prevent detection and hide the malicious code in an advertisement’s images.
The campaign has been analyzed by both Confiant and Malwarebytes and the researchers believe that it has been active since January 11 and lasted until January 13. The infected ad was viewed over 5 million times during the time that it was active.
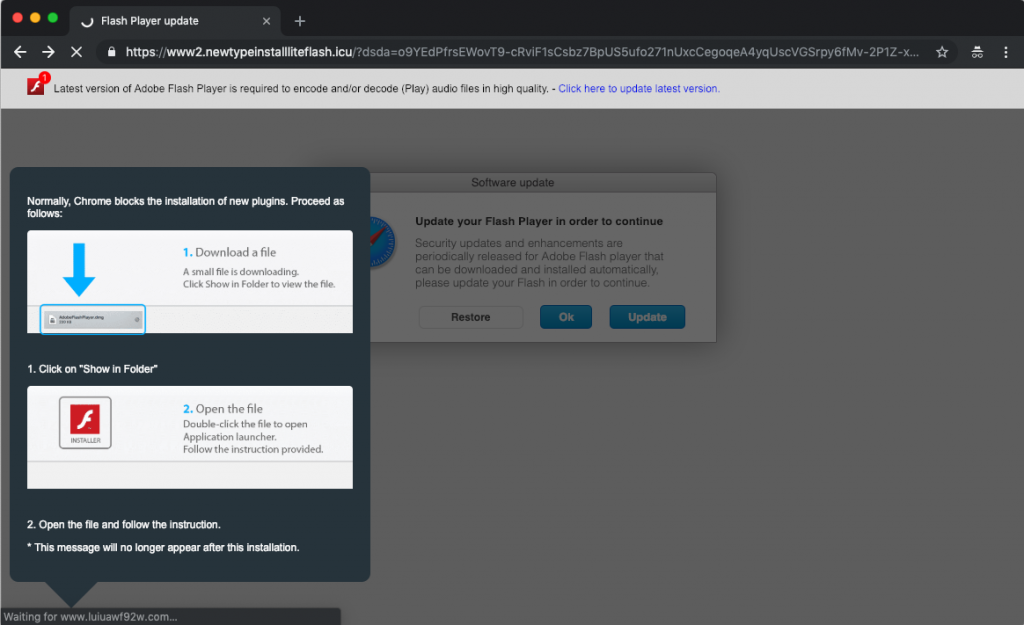
Ad viewers claim that the campaign involved a tried-and-tested tactic of displaying a notification that the user needs to update the Adobe Flash Player and to do this the user has to open a file to download the new version. Whoever accepted the download ended up running malware on their Mac and the device was infected with the Shlayer Trojan.
“As malvertizing detection continues to mature, sophisticated attackers are starting to learn that obvious methods of obfuscation are no longer getting the job done. Techniques like steganography are useful for smuggling payloads without relying on hex encoded strings or bulky lookup tables,” Confiant researcher Eliya Stein revealed.
It is a noteworthy attempt from VeryMal because usually, attackers find it difficult to evade the numerous protection layers of the ad networks and user desktops. But, VeryMal successfully hides the payload within the ad’s graphics file using steganography. The code can create a Canvas object, extract an image file from a certain URL, and create a function to check if the browser supports a particular font.
In case the font check fails, the campaign won’t work, but if it is successful then the image file’s underlying data is looped through and each loop determines a pixel value that later becomes an alphanumeric character. The character is later converted into a string and executed.
However, despite harboring the payload, the image is harmless itself if someone views it and only becomes harmful when the malicious code is executed and the browser is redirected to a link containing the payload.
Mac users are urged to remain alert and don’t pay heed to all the online notifications that they see on their desktop screens because it may be a part of malvertising campaign. They should specifically be wary of notices that ask users to install software updates and provide an unofficial link for the download.
What happens in steganography is that hackers extract the file and hide malicious code in image’s User Comment EXIF metadata field.
This is not the first time that hackers have used steganography technique to drop malware. Just last month, researchers discovered two memes hiding commands in their metadata with the help of steganography spreading malware on Twitter.
In another attack, malicious images were hosted on GoogleUserContent CDN using steganography, however, what’s shocking is that these attacks are not limited to computer users. Back in 2016, steganography was also used for deploying over 60 malicious applications on Play Store.