A side-channel vulnerability existed in the implement of the CSS3 feature called “mix-blend-mode.” It allowed an attacker to de-anonymize a Facebook user running Google Chrome or Mozilla Firefox by making them visit a specially crafted website.
The flaw, now fixed, was discovered last year by the researcher duo Dario Weißer and Ruslan Habalov, and separately by another researcher named Max May.
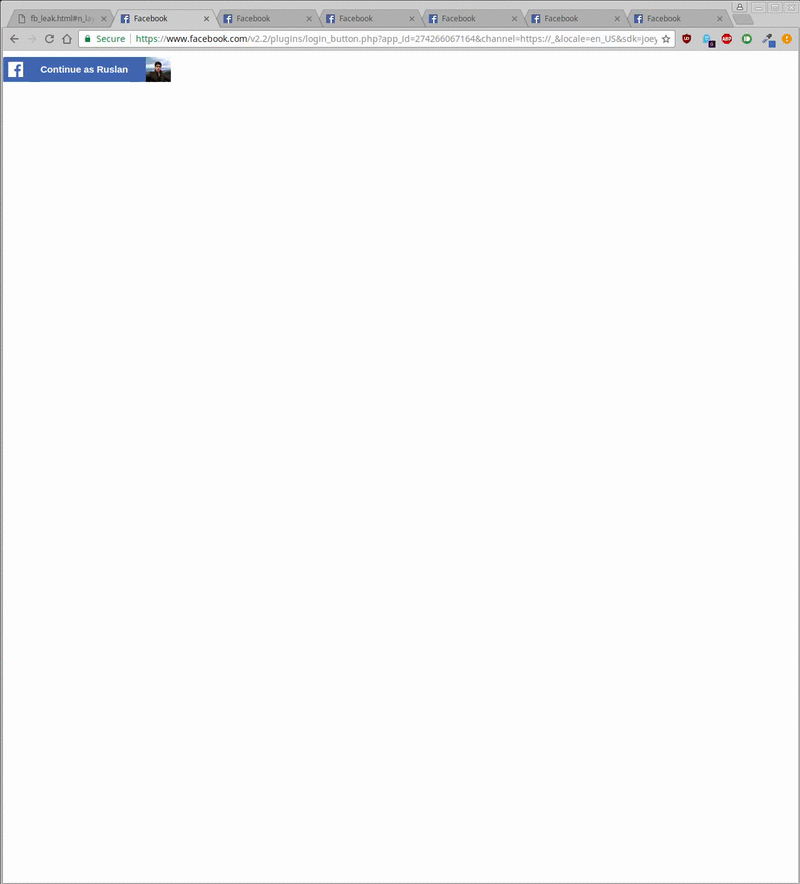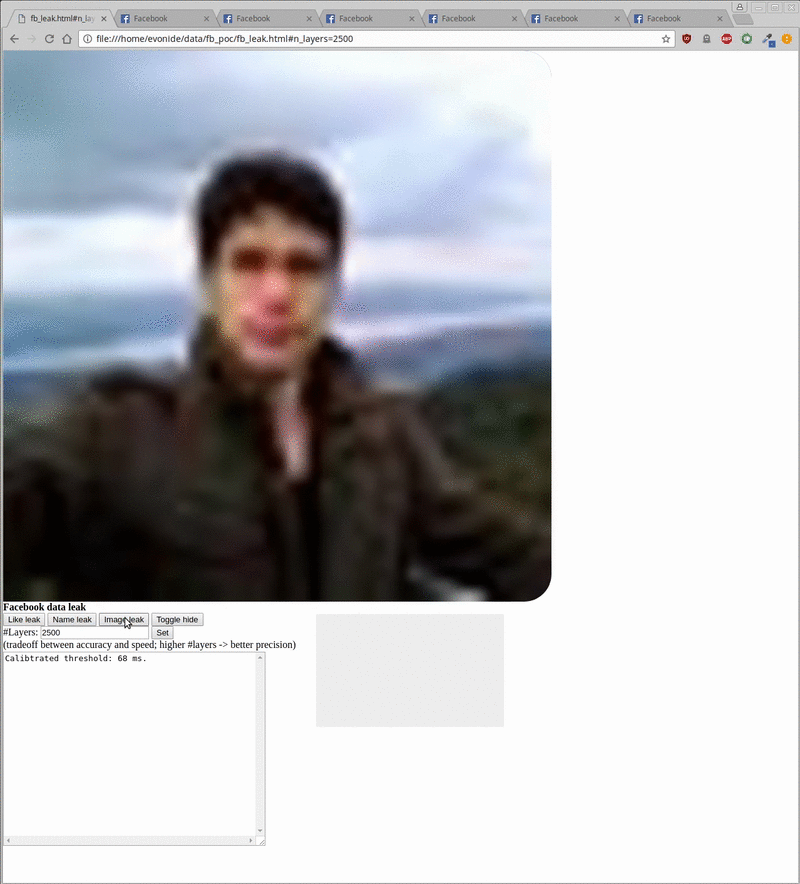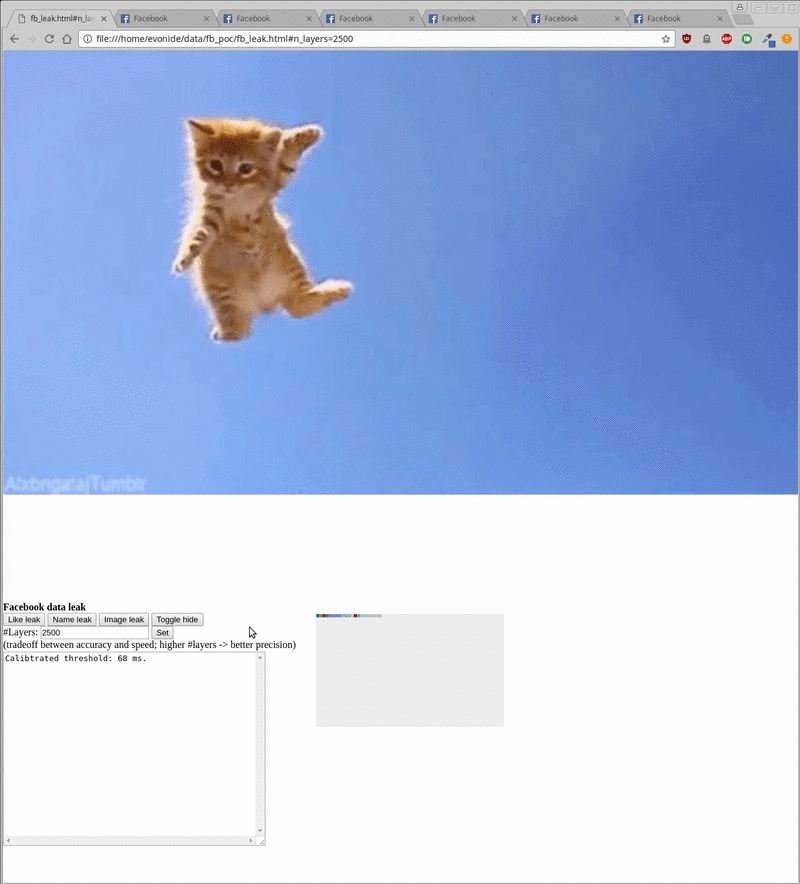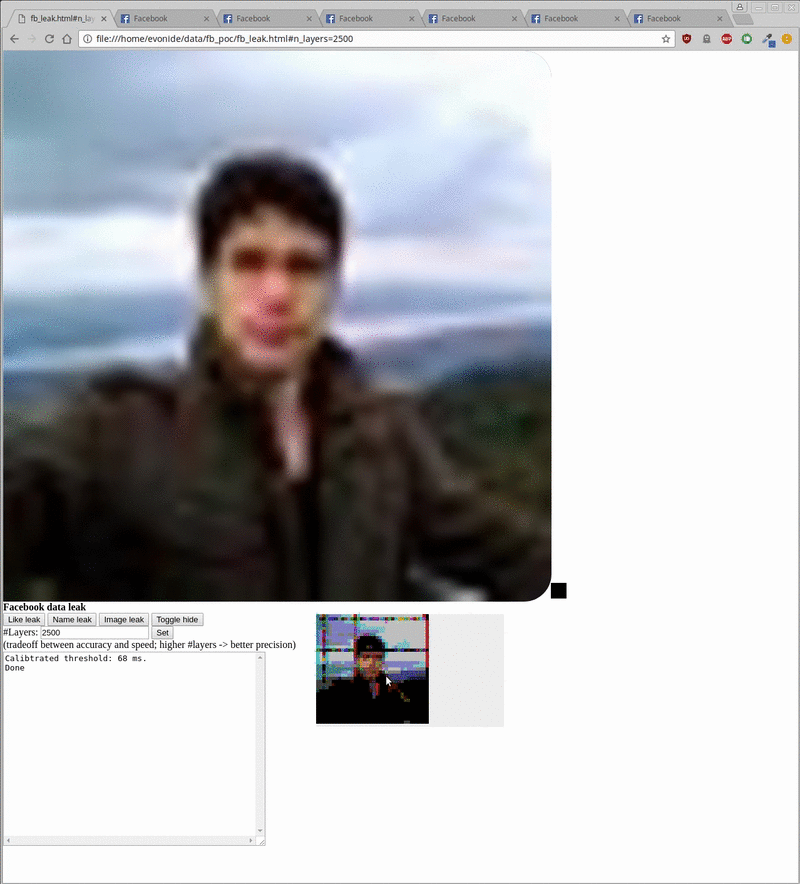
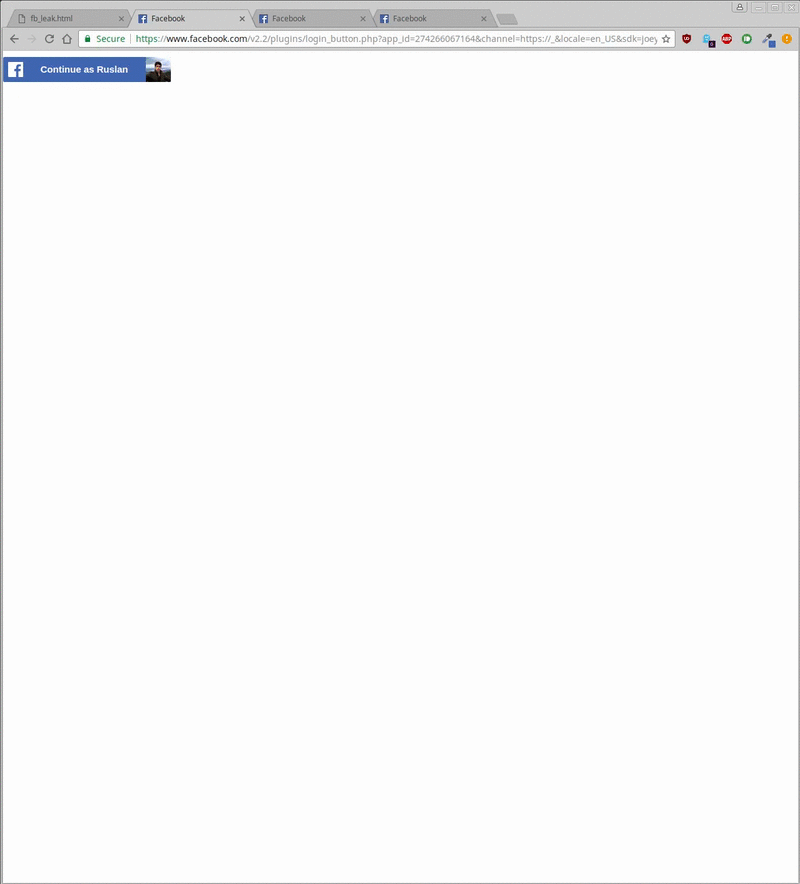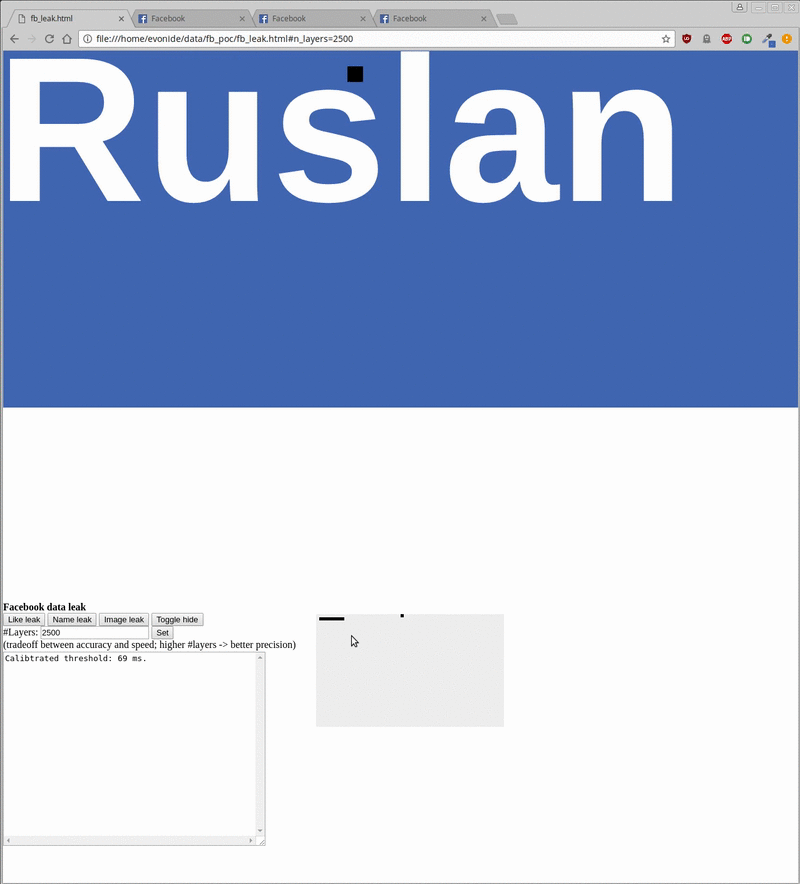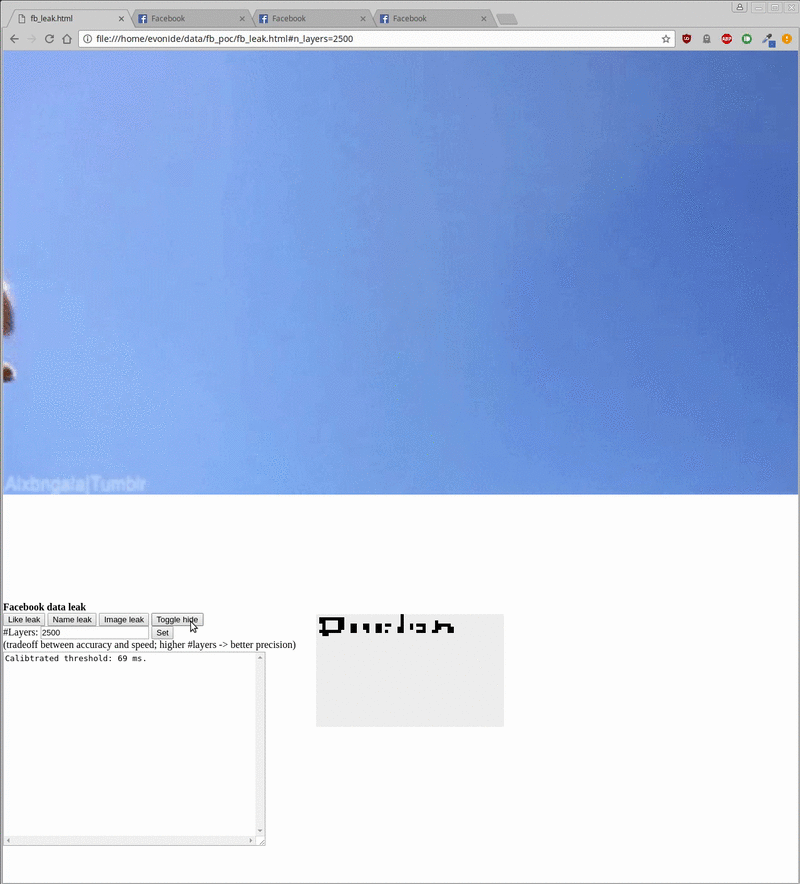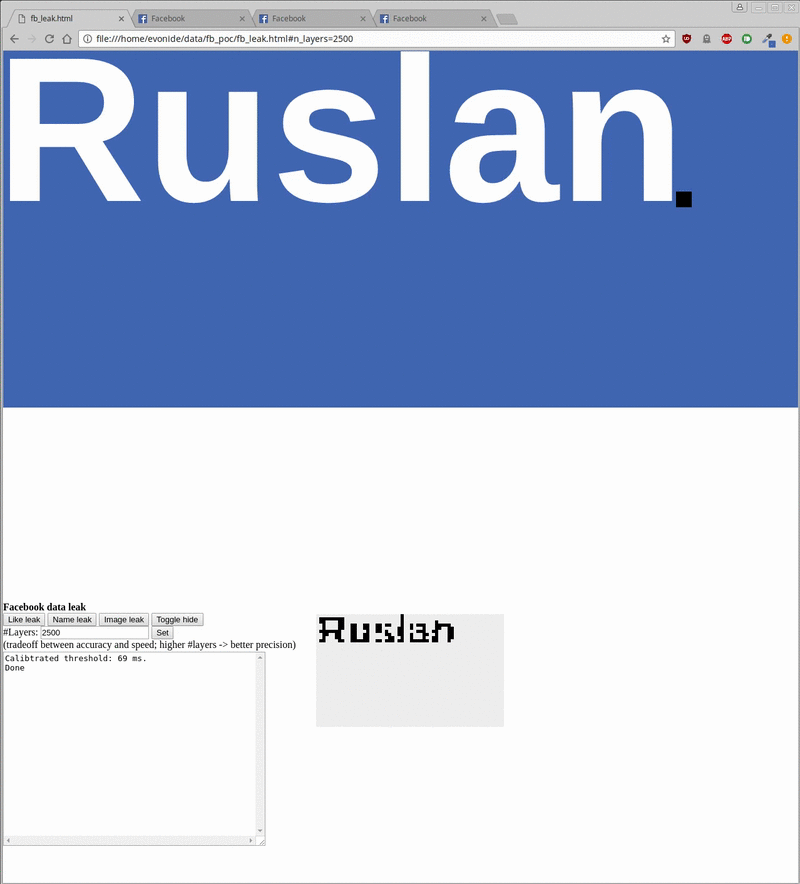
The proof-of-concept created by the researchers enabled them to harvest data like the profile picture, username, and ‘like’ status of unsuspecting visitors, the researchers said in their blog post. All of this could be done in the background when a user visits a malicious site.
The visual data leak could happen on websites using iFrames that link to Facebook in the form of social plugins and login buttons. Because of a security feature called same origin policy, websites can’t access the content of iframes directly. The researchers can extract information by creating an overlay on the cross-origin iFrame to interact with the underlying pixels.
The POC takes around 20 seconds to reveal a username, around 5 minutes for a vague version of the profile picture, and around 500 milliseconds to check the like status of a given site. However, target user should be logged into their Facebook account for the method to work.
Both Google and Mozilla were notified privately by the researchers. However, it was made temporarily public last year as the independent researcher Max May had already posted it on the Chromium mailing list in March 2017.
The side-channel vulnerability was fixed for Google Chrome in December last year (version 63). For Firefox, the patch was made available two weeks ago (version 60). That’s because the researchers encountered some error that delayed the disclosure to Mozilla until November 2017.
The exploit didn’t affect IE and Edge as the web browsers don’t support the required feature. Safari wasn’t affected either for some reason.
While the flaw has been patched for good, the researchers warn that the advanced graphics capabilities added to HTML and CSS could open doors for more attacks like these.
Via ArsTechnica