The hacker organization known as Cl0p has said that they are responsible for breaking into a number of educational and government organizations, including the University of Georgia. Now, the hacker organization has claimed responsibility for breaking into Norton Lifelock, which is a service that is used to safeguard people’s credit after their identity has been stolen. The attack took use of a zero-day vulnerability in the MOVEit Transfer managed file transfer (MFT) software that Progress Software reported on May 31. The vulnerability was exploited by the attacker. Gen Digital, the company that is responsible for well-known cybersecurity brands such as Avast, Avira, AVG, Norton, and LifeLock, has acknowledged the effect of the ransomware attack and disclosed that the attackers compromised the personal information of workers. This information includes names, residences, birth dates, and business email addresses.

The company confirmed, they have remedied all of the identified vulnerabilities in the system and utilize MOVEit for our file transfer needs. As soon as they became aware of this situation, they took prompt action to safeguard their ecosystem and assess the implications of any possible fallout. They have verified that there was no effect to our essential information technology systems or services, and that no data pertaining to either customers or partners was made public. Unfortunately, certain employees and contingent workers of Gen had some of their personal information compromised, which includes information such as their names, corporate email addresses, employee ID numbers, and in a few isolated instances, their home addresses and birth dates. They immediately began an investigation into the breadth of the problem, and consequently have informed the appropriate data protection agencies as well as our workers whose personal information may have been compromised.
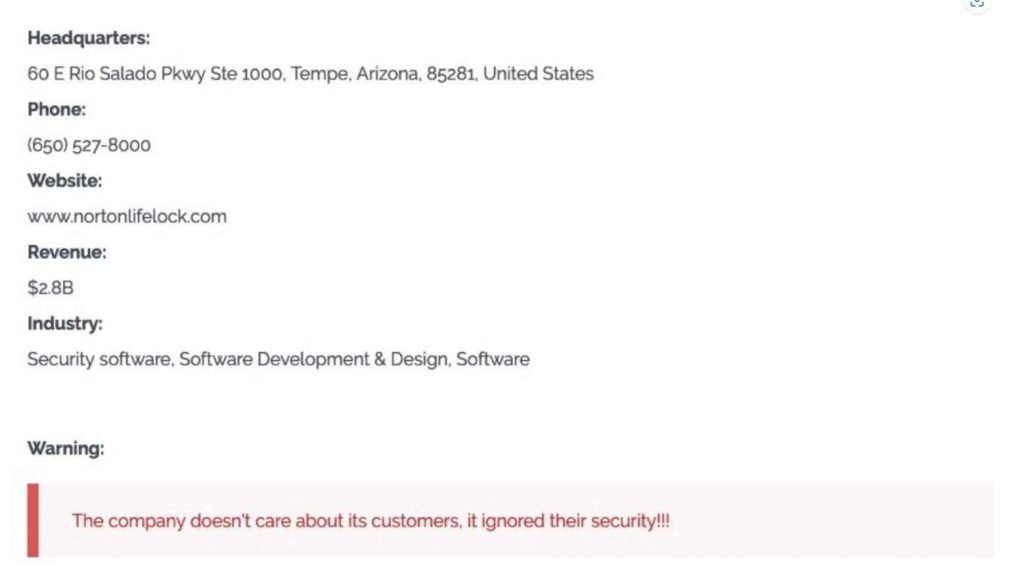
Independently, we were able to confirm that the dark website operated by Cl0p included a listing of Norton Life Lock as one of the group’s more recent victims. On the website, Cl0p writes the following about Norton: “The company doesn’t care about its customers, it ignored their security!!!”
MOVEit zero-day revelation led to the discovery of two other critical-severity SQL injection issues in the MFT program. These bugs were designated as CVE-2023-35036 and CVE-2023-35708 respectively.
Progress Software has recommended users to deploy updates for them as soon as possible, even though none of them has been exploited in attacks to this far. This is to prevent unauthorized access to the MOVEit Transfer environment.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.