US Financial Institutions and banks Threatened by Deadly New Version of Dridex Malware
Once upon a time, there was a malware called Dridex, which was a preferred attacking tool of hackers and threat actors but then it lost its spark and we all forgot about how devastating it was. But the malware is back with a bang and its upgraded version is much scarier than its predecessor.
Dridex malware’s newest version is extremely dangerous and it is threatening US-based financial institutions big time. Reportedly, Dridex banking malware has become the preferred tool for cyber-criminals and is now being used extensively in their latest campaign against US-based banks.
Must Read: GozNym Malware Hits Banking Systems in Canada and The US
The researchers Rhena Inocencio, Michael Casayuran and Jay Yaneza of Trend Micro have reported about the revival and resurfacing of this malware after they identified an extraordinary rise in Dridex spam emails this May. The firm also revealed that about 59.7% of the attacks have been spotted against US targets while Brazil and China came at number two and three respectively.
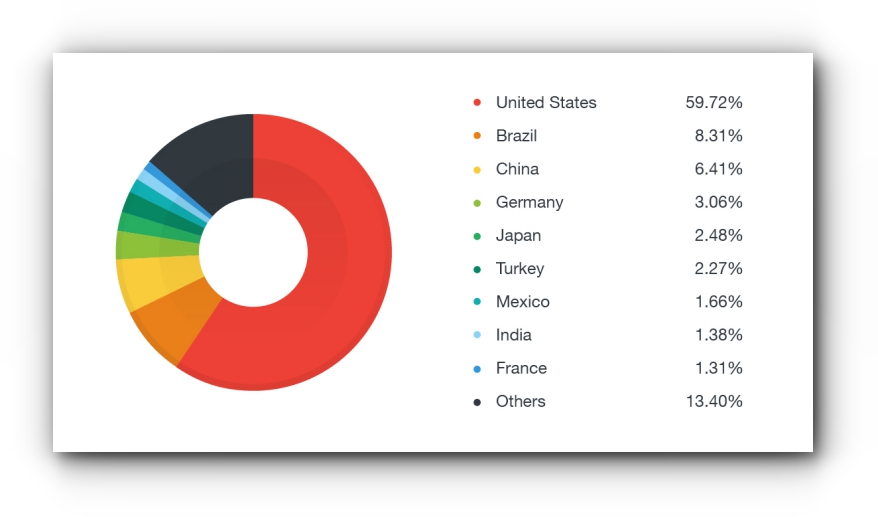
Image Source: Trend Micro
As per the researchers, this latest iteration has donned a new avatar as it no more uses bogus invoices and notifications to deceive the user but lures the victim into opening a spam email and click on the attached file, which is obviously infected with malware. Moreover, the malware has been paired with Certuli, a command-line program. This program lets the malware look like a genuine certificate.
According to the analysis of Trend Micro, it is a challenge to detect and mitigate Dridex attack. The security firm notes that:
“Prior to this new wave, the use of macros enables the threat to bypass sandbox technologies. This clearly indicates that DRIDEX is leveling up its ante to remain a prevalent online banking threat.”
These changes have made this malware a very hard to eradicate banking threat.
In their report Trend Micro researchers identified that this email message contains the subject line “Account Compromised,” and it contains information about the supposed “login attempt including the IP address,” so that the email appears authentic.
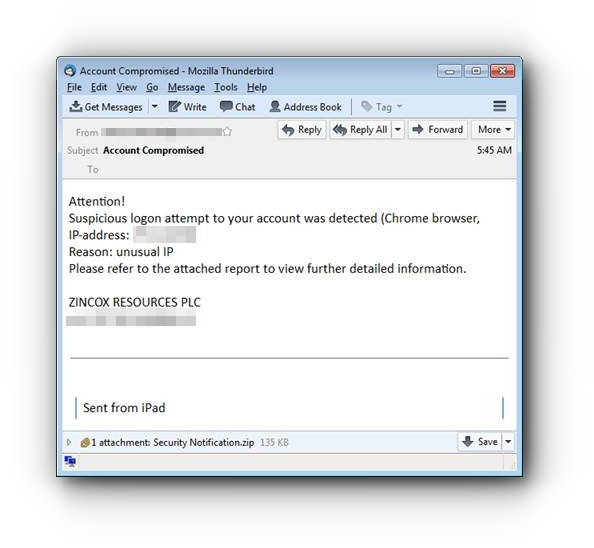
If you receive similar email don’t download any attachment and don’t click on any link / Image Source: Trend Micro
Further, the research team wrote that:
“The spammed message is almost believable except for one missing crucial detail: It doesn’t have any information on what type of account (email, bank, social media accounts etc.) is compromised.”
[fullsquaread][/fullsquaread]
The company so far is unsure if this new version can prove to be as effective as its earlier version. So be careful while opening any email that comes with attachments. If you have received any such email contact us and we will get the sender blocked.
[src src=”Source” url=”http://blog.trendmicro.com/trendlabs-security-intelligence/dridex-poses-as-fake-certificate/”]Trend Micro[/src]