The US-based cryptocurrency exchange service Poloniex, which happens to be the largest exchange service in the world with over a hundred types of cryptocurrencies available for trading/buying, has been in the news lately for all the wrong reasons.
In August 2017, we reported that a security researcher managed to bypass the 2FA (two-factor authentication) process at Poloniex. Using Reddit handle Poloniex2FASucks the researcher revealed that he waited for 60 days for the company to respond and fix the issue but ultimately sold the vulnerability.
According to a blog post by Lukas Stefanko of ESET Security firm, Poloniex users are being targeted by two fake credit stealing applications that appear to be legitimate Poloniex Android apps. These apps are available on an authentic and reliable platform like Google Play Store and are capable of not only stealing the victim’s Poloniex website login credentials but also end up accessing the Gmail accounts of the victim, which are then hijacked by the attackers.
It is worth noting that there is no official mobile app launched by Poloniex yet and this is the very aspect that is being exploited successfully by cybercriminals. Given the high profile nature of Poloniex, as it is world’s leading cryptocurrency exchange service, it comes as no surprise that cybercriminals have set their eyes on this particular organization.
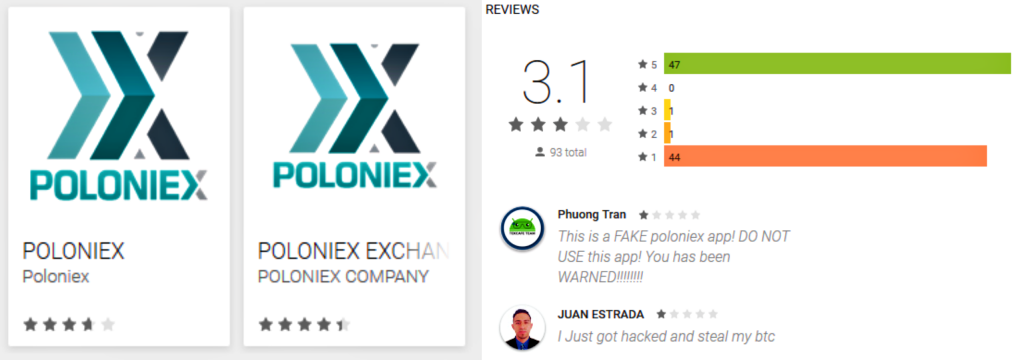
The first of the two malicious apps is called POLONIEX. It is available for download on Google Play and published by a developer named Poloniex. Despite the bad reviews and low ratings of the app, it was downloaded and installed by more than 5000 users between 28 August and 19 September 2017.
Another fake app is called POLONOEX EXCHANGE. It is published by a developer named POLONIEX COMPANY. It was uploaded on Google Play on October 15, 2017, and within just a week it has been installed by 500 users. After ESET notified Google about the malicious nature of the app, this was removed from the store.
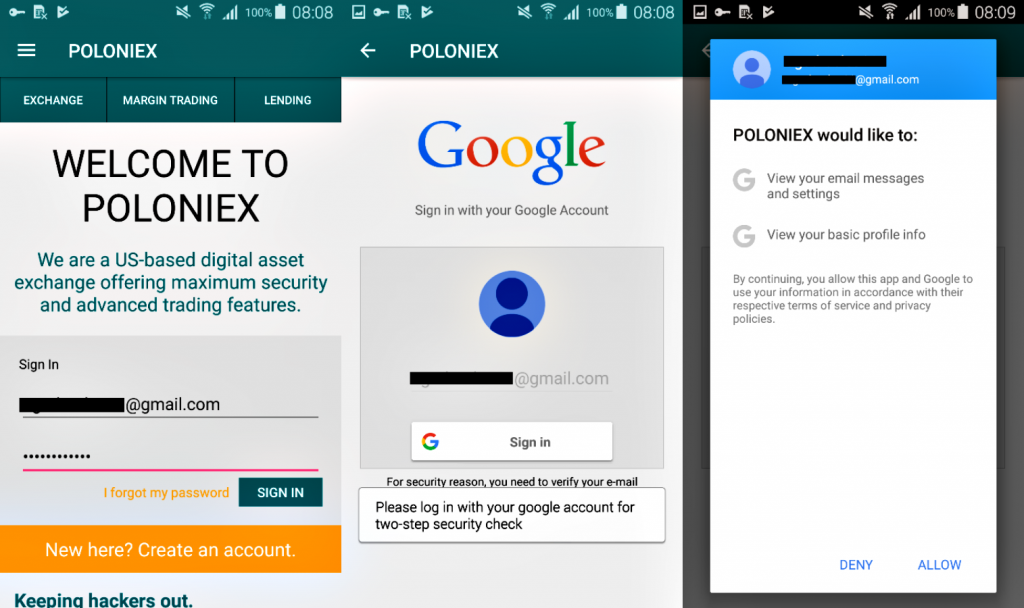
To hijack Gmail accounts and obtain Poloniex credentials of unsuspecting users, these apps use the same method. As soon as the app is launched after installation, it displays a fake Poloniex message box asking for login credentials. When the victim enters the credentials and clicks on Sign In, the attacker receives the credentials. This method is successful when the user hasn’t enabled 2FA on the Poloniex account.
When attackers get the credentials, and 2FA is not enabled, then they can easily access the account and perform transactions on behalf of the user. They can also change account settings and change the password to lock the account. Afterwards, attackers try to gain control of Gmail account of the victim. The user is sent a message that appears to be sent by Google.
In the message, the user is asked to enter Gmail account login details to complete the Two-Step Security Check. When the user clicks on Sign In, the app requests for permission for accessing the email messages and settings as well as explore basic profile. If the permission is granted the app successfully accesses the inbox.
After accessing the Poloniex account and the Gmail account linked with the exchange service, the attackers manage to make transactions through the hijacked account and remove all signs of unauthorized access and transactions from the inbox. Lastly, the app requests the user to download the mobile version of the authentic Poloniex website and then the user is asked to sign in.
On the other hand, if 2FA is enabled then the account will remain protected from being hijacked because now Poloniex is providing 2FA through Google Authenticator which involves generation of random login keys that are sent to the users as a text message, voice call or through the Google Authentication app. Attackers cannot access any of these.
To ensure that you stay safe from the malicious apps then change your Poloniex and Gmail account passwords as soon as possible and if you have installed any of these fake apps, delete them immediately. Also, enable 2FA authentication for both services.
Also, make sure that the service you are using does have a mobile app and only download the mobile app from the official website of the service. Moreover, never ignore user ratings and reviews about a particular app and install a reliable mobile security product.
[fullsquaread][/fullsquaread]