The infection chain starts when the victim clicks on an ad from Google on the search results page.
SentinelLabs researchers have identified a new targeted campaign delivering ZLoader banking trojan. The malware is also known as ZBot and Silent Night which has been spreading its infection since 2016.
It is worth noting that ZLoader was a feature-rich banking trojan back then and was believed to be a fork of ZeuS banking malware. Its subsequent versions implemented a VNC module that granted adversaries remote access to infected systems. Since then, the malware has been in active development, and recently a new version of ZLoader has been identified.
Previous Coverage
Hackread.com has been actively following ZLoader campaigns since it was first discovered. In 2020, ZLoader was detected by Check Point researchers in multiple CV-themed campaigns targeting users in the US, UK, and Romania. In that campaign, organizations were tricked into downloader the trojan through fake CVs sent to their official email accounts in Microsoft Excel attachments containing the malware.
SEE: Malicious Office documents make up 43% of all malware downloads
The notorious malware made another appearance in July 2021, when McAfee Labs reported that threat actors used non-malicious documents to disable security warnings before executing macro code on the victim’s computer. Hackers, hence, devised a new tactic to execute malicious DLLs/ZLoader.
About the Latest Wave of Attacks.
The latest campaign involving ZLoader is believed to be targeting financial institutions in Australia and Germany. The campaign aims to intercept users’ web requests made to the banking portals and steal banking credentials.
To stay under the radar, threat actors have included a series of commands to disable Windows Defender. The trojan is distributed via Google AdWords once all Windows Defender modules are disabled on the targeted machine.
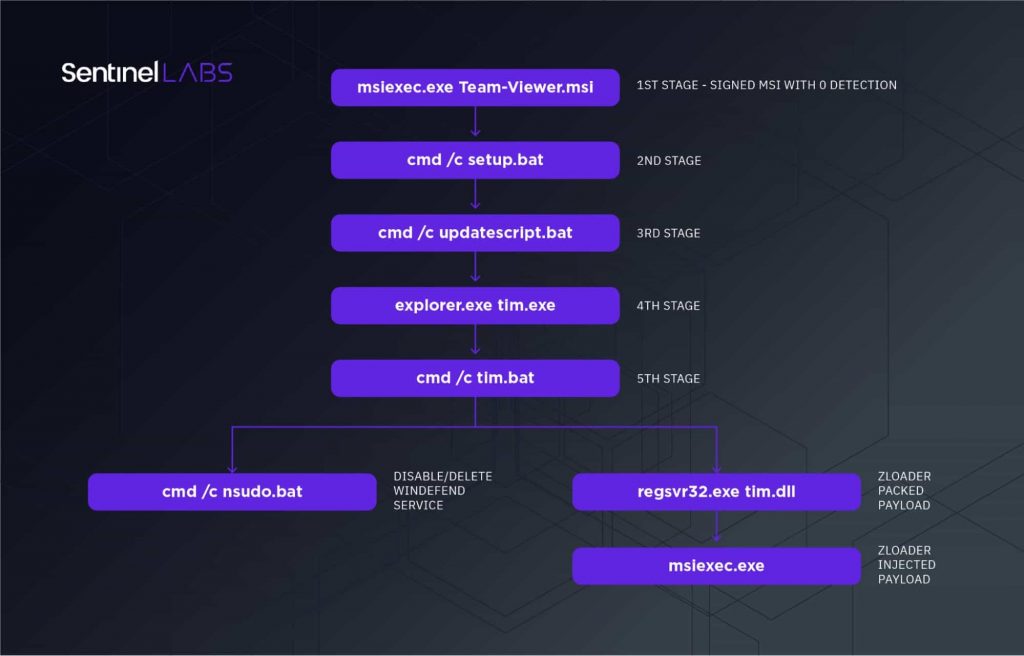
According to Sentinel Labs researchers, the infection chain includes a signed dropper and a backdoored version of the Windows utility wextract to embed the ZLoader payload.
Beware of Fake TeamViewer Downloader
The infection chain starts when the victim clicks on an ad from Google on the search results page. The user is then redirected to a bogus TeamViewer site, which the attacker controls. Hence, the victim is tricked into downloading a signed but fake variant of the software, titled Team-Viewer.msi.
The fake installer serves as the first stage dropper, after which a series of malicious actions commences, including downloading the next-stage droppers to impair the machine’s defenses and eventually downloading the ZLoader DLL payload.
Researchers also noted that in some cases, popular apps like Zoom and Discord were exploited, indicating that multiple threat actors could be involved or multiple campaigns are active at the moment.