Security researchers have found out that the latest version of the ever-popular Genieo installer adware has fetched a new system to access the Mac Keychain without any prior involvement from the user, allowing this adware to access and distribute sensitive data and user credentials stored within the credential manager.
In a nutshell, what Genieo adware does is to gain access to the Keychain feature in OS X, which is aimed to help users by preventing them from entering their account credentials several times when re-accessing the account. Keychain stores login credentials for all your web-based accounts including Gmail, Outlook, Apple, iCloud.
[must url=”https://www.hackread.com/ios-jailbreak-backdoor-tweak-icloud-hacked/”]iOS Jailbreak Backdoor Tweak Compromised 220,000 iCloud Accounts[/must]
For those who are not aware of this adware, it is designed and circulated by Genieo Innovation that is an Israel-based company that is renowned for its malware and other harmful apps. The latest version of their adware installer has not been blocked by Mac OS X anti-malware protections and automatically redirects the user to Download Shuttle’s App Store version.
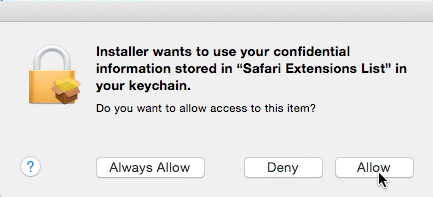
According to the researcher Thomas Reed over at Malwarebytes, who is apparently the first one to discover this vulnerability, prior to the installation of this Genieo installer, it exploits the vulnerability by asking user for a permission to verify their password. Then it installs a Safari browser extension called Leperdvil that asks for keychain access by displaying a dialogue box asking whether to allow or deny the access.
The dialogue box generate by the extension doesn’t prompt for any password, however, the user will notice that, within a fraction of a second, the extension automatically clicks on the “Allow” button. This happens instantly that the user don’t even get a moment to react. It is believed that many would not even notice the dialogue box.
Check the demo video below to see this in action:
[must url=”https://www.hackread.com/apple-phishing-scam-govt-site/”]A Compromised .GOV URL Hosting Phishing Attacks on Apple Users[/must]
This unusual activity of Genieo installer makes it much more dangerous for its users and could become a great probability for abuse by attackers who might exploit it. These type of autonomous actions could easily be implemented in other apps and installers to exploit Keychain access dialogue box.
Until now, there is no statement released by Apple, but speculations reveal that the company might fix this issue in the next release of OS X.
So to protect your computer and the data stored on your OS X, it is recommended to avoid downloading apps and files from mysterious sources.
Suggest ideas, report typos and corrections to [email protected]
[src src=”H/T” url=”https://blog.malwarebytes.org/mac/2015/08/genieo-installer-tricks-keychain/”]Malwarebytes[/src]