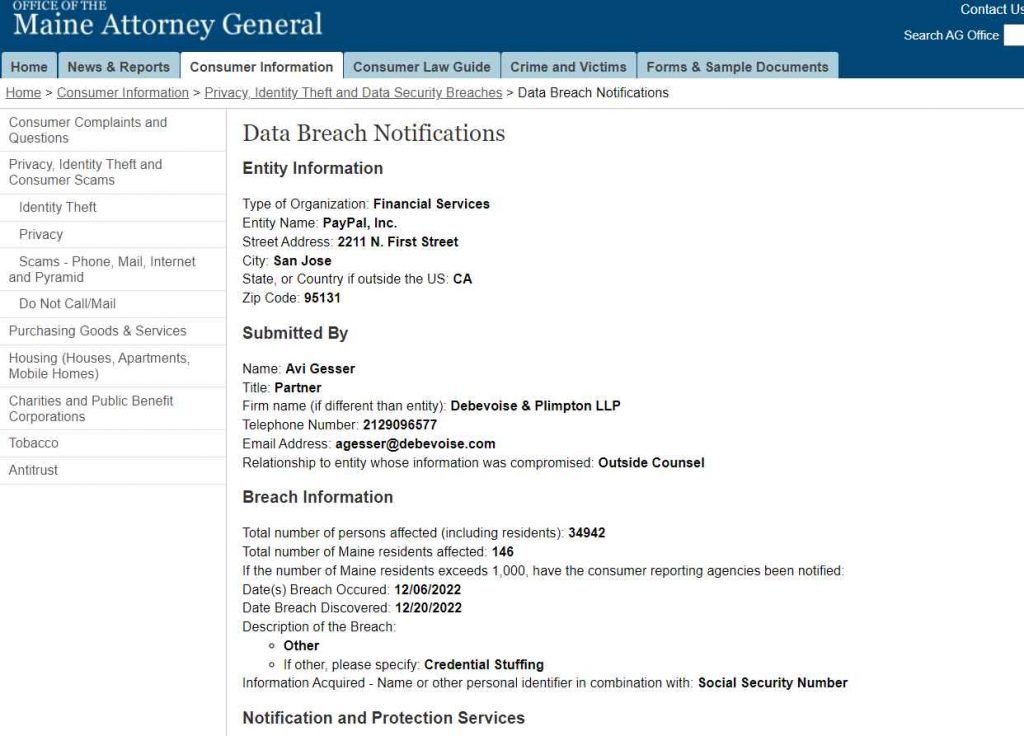
After a credential stuffing attack on December 6, which gave hackers access to names, addresses, Social Security Numbers, individual tax identification numbers, and dates of birth, PayPal is in the process of mailing breach notification letters to almost 35,000 of its customers.
The breach, which took place between December 6 and December 8, was brought to the attention of the Attorney General of Maine by the corporation.
On December 20, PayPal revealed that hackers gained access to personal data and financial information by using credential stuffing attacks. These attacks were used to obtain access to personal data.
Hackers carry out a credential stuffing attack when they take username and password combinations that have been compromised as a result of data breaches and try to use them at other online services in the hope that some users reuse credentials across other websites.
PayPal has said that their platform has not been compromised, and they have written that there is “no indication” that client login information have been stolen “from any PayPal systems.” Instead, access was gained to them via a preexisting data breach.
The letter states that “We have not delayed this communication as a consequence of any law enforcement inquiry.” It also mentions that the firm has changed the passwords of the accounts that were compromised and will need the customers to generate new login credentials when they try to log back in.
In addition, Equifax will provide victims with two years’ worth of free services, which will include credit monitoring, fraud alerts, identity restoration, and up to one million dollars’ worth of identity theft insurance coverage for a predetermined list of out-of-pocket expenses that resulted from identity theft.
Despite the attempts of law enforcement to shut down the markets and prosecute individuals selling the login data, there are multiple dark web forums where thousands of PayPal credentials are sold to customers.
Fraudsters may now employ bots to try thousands of logins within seconds using hacked user credentials. This can be done with the help of automated software.
PayPal is one of the firms that is impersonated more than any other, both in phishing emails and in other kinds of fraud efforts.” “When using PayPal, always double check that you are logging onto the official website. Check the URL for any spelling mistakes, and under no circumstances should you click on any links or attachments included in unsolicited emails.
Hackers use automated tools to scan previously produced lists of compromised usernames and passwords. Bots enable hackers to conduct millions of login attempts “with very little effort on their behalf.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.