Dubbed Skidmap by researchers; the Linux malware mines cryptocurrency and drops backdoor – All that without being detected.
The perception cryptocurrencies have created today ranges from them being a “flat out scam” to an innovative piece of technology in the new age. While our understanding of the latter is clear, the former needs some light to be shed on, how did we get here?
To answer this, we may look no further than the latest in the cryptocurrency world where another Linux malware named as Skidmap has been discovered by Trend Micro that illegally mines cryptocurrencies, a malicious technique known as cryptojacking.
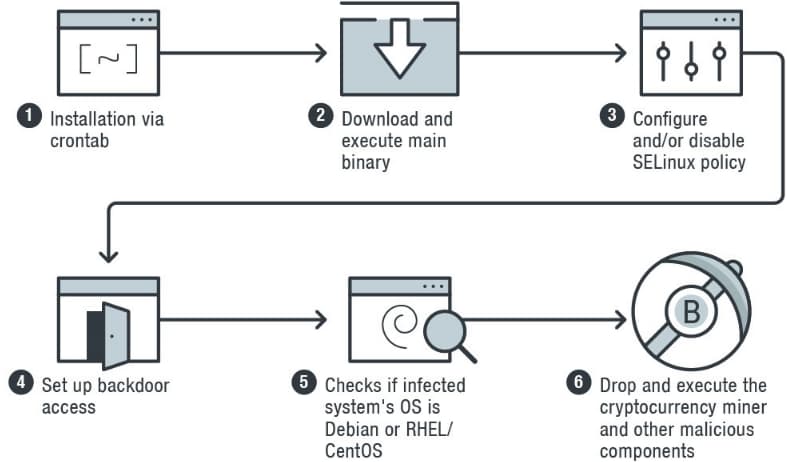
The malware works in such a way that initially, it creates malicious loadable kernel modules in Linux modifying and overwriting other kernel parts which help it avoid detection. Additionally, the malware will install itself through the crontab module in Linux which allows one to regularly schedule commands.
After the installation, a main malicious binary is downloaded which is responsible for reducing the security of the device to engage in cryptojacking. After this phase, it moves on to create backdoors by generating a secret password allowing access to the infected advice. It does this by making the binary previously installed to add the public key of its handlers to a file called authorized_keys.
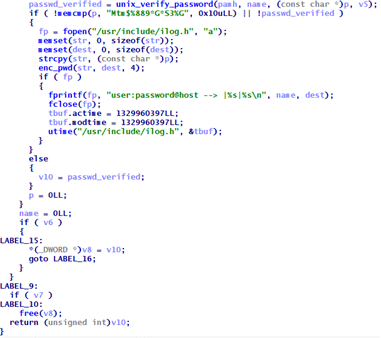
As evident from the name, this then allows the malware to use its own key to authenticate itself and get into the system. But it doesn’t end there. A second method is also employed where the system’s “pam_unix.so” file which is responsible for authentication in a UNIX system is replaced with a malicious version known as “Backdoor.Linux.PAMDOR.A”. This then allows the computer to accept certain passwords for any user allowing unrestricted access even if other accounts on the system were not compromised.
Coming to the crypto part, the malware checks the system’s OS and drops the miner accordingly. For example, if it is Debian based, the payload is dropped to “/tmp/miner2” and if it is CentOS/RHEL based,
it will download a tar (tape archive) file from the URL, hxxp://pm[.]ipfswallet[.]tk/cos7[.]tar[.]gz, containing the cryptocurrency miner and its multiple components, which is unpacked and then installed. Of note is that the content of the tar file is decrypted via OpenSSL with the key “jcx@076” using Triple DES cipher, as stated by the Trend Micro.
Yet, it doesn’t end there. Other malicious components were also found which include the following:
- A fake “rm” binary that replaces the original “rm” command which is used for deleting files. This is being used to download and execute files with the help of a cron job randomly run.
- A kaudited binary which as mentioned before is used to install loadable kernel modules.
- An iproute module to hide specific files.
- A netlink rootkit to alter network and CPU-related statistics. This is essential as if the user realizes that the CPU’s load is high despite little usage on their behalf, this would be a clear red flag alerting them of some malicious activity.
To conclude, we’re usually susceptible to Windows’ security due to its reputation of being often infected with malware ranging from plain viruses to ransomware. However, the fact that Linux is also in the same loop should be alarming to users out there because despite it having more technically advanced users, it still remains vulnerable.
Simple precautions such as keeping your system up-to-date, keeping administrator privileges for the least possible number of users and being wary of common attacks such as phishing can go a long way and help you remain safe.
This, however, is not the first time when a Linux malware has surfaced to mine cryptocurrency. To name a few, SpeakUp, Xbash, EvilGnomes, Setag, and Bird Miner, etc. are some of the active threats against Linux users.