According to a French researcher, the renowned antivirus vendor McAfee sent s file loaded with Emotet banking malware to customers using its anti-hacking service called ClickProtect email protection service. Although Emotet malware was hosted on a third-party website it was shared through a domain that was linked with the project. Ironically, McAfee marketed the anti-hacking service as a fool-proof solution for protecting the business from being hacked. The purpose of ClickProtect was to prevent users from phishing attacks, infected websites, and malware.
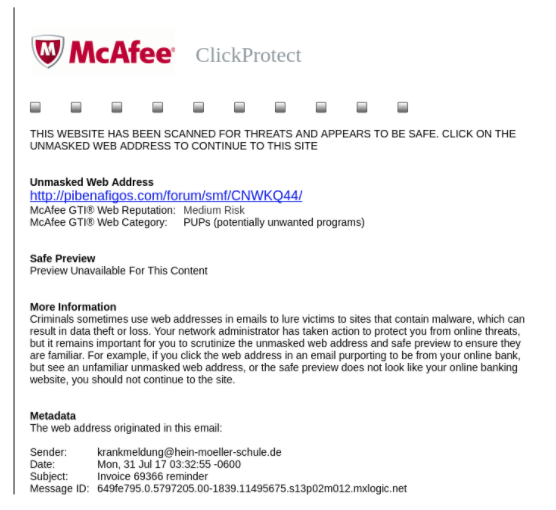
ClickProtect scan result
The Paris-based researcher who uses the alias Benkow discovered the malware, and he reported about it via Twitter where he explained that ClickProtect rewrites all the web links in an email message with the one using the domain “cp.mcafee.com” and after this, it analyses the link to check if it is malicious or safe. The link is then scanned every time somebody clicks on it.
cp.mcafee.com can seriously be used for spreading malware ?! (link still works) https://t.co/oGbAVgXQoM pic.twitter.com/DvSlpFKfiP
— Benkow moʞuƎq (@benkow_) November 13, 2017
However, according to Benkow, a URL registered with the ClickProtect’s domain under McAfee leads to an infected MS Word document which contained Emotet banking malware. This means, if someone downloads the Word file, he or she will be instantly exposed to Emotet.
Emotet is a dangerous banking malware that gains financial information of a user simply by injecting malicious coding in the computer’s network stack, and it is delivered through infected URLs. Attackers hide these malicious links in emails, Word files, and PDFs.
As per Malwarebytes’ chief malware intelligence analyst Jerome Segura, Emotet is widely distributed through “malspam campaigns” that contain links to infected websites hosting a malicious Word document. When a user opens this file, it triggers the macros, and Emotet malware binary is downloaded. The malware utilizes PowerShell script to get additional information.
Further assessment revealed that this is not a new occurrence because previously Salesforce.com administrator observed similar problem a few years back. This shows the malware has been upgraded numerous times in recent years to make it powerful enough to evade detection. Apparently, this malware is used as a dropper to spread another banking malware called IcedID.
After getting installed, the malware obtains information like card numbers and passwords, which is used to hack into user’s accounts and transfer their money online. It can also hack the C&C center of a compromised computer and use hard-coded IP addresses to generate proxies and prevent detection.
When notified about this issue, McAfee responded by investigating Benkow’s discovery and identified that the ClickProtect feature was operating properly and that the researcher’s concerns “arose out of the timing of ClickProtect’s reputation-based status detection and response.”
According to the official statement from McAfee’s Global Threat Intelligence service, until the early hours of November 13 this web link was not identified to be distributing the malware but later on they identified this link as a threat, and therefore, its reputation rank was changed from low risk to high risk and McAfee customers were blocked from accessing this link. However, according to ZDNet, the link was still accessible until Thursday, and it wasn’t blocked as well as claimed by McAfee.
Segura further stated that to stay protected users need to avoid clicking on converted or shortened links. Similarly, they need to be cautious of emails that show signatures added at the end of an email claiming that the email is Virus-Free because it makes users feel safe while opening an attachment but they don’t know that criminals also add such messages through social engineering tactics.
Remember, Benkow is a credible IT security researcher who in May this year found killswitch for the new variant of WannaCry ransomware. Moreover, he also discovered “Onliner Spambot” dump containing 711 million email and passwords of users around the world.
[fullsquaread][/fullsquaread]









