The infamous Mirai botnet lets threat actors use compromised devices to carry out large-scale and crippling DDoS attacks.
Critical Microsoft Azure vulnerabilities reported and patched earlier this week are actively exploited by threat actors and cybercriminals. Dubbed the OMIGOD flaws; the vulnerabilities were originally discovered by the Wiz Research Team.
READ: Microsoft warns of Azure flaws exposing users to data theft
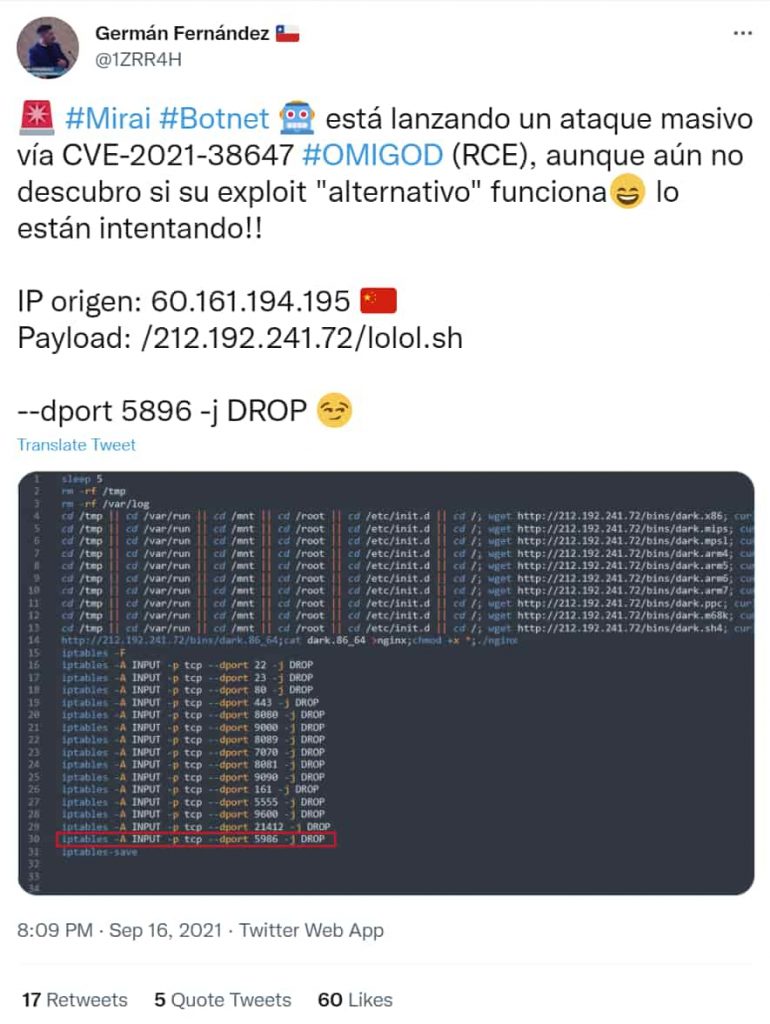
On the other hand, security researcher Germán Fernández identified one of the botnets trying to exploit the reported vulnerabilities. Fernández tweeted that attackers are searching for Azure Linux virtual machines as these are vulnerable to a remote code execution flaw identified in Azure.
This finding was confirmed by Bad Packets security firm.
The researcher also highlighted that a Mirai botnet operator is one of the attackers scanning the web for vulnerable machines. ThreatModeler’s director of strategy, Stuart Winter-Tear, explained that it is important to close any open OMI ports to prevent exploitation.
In a conversation with Cado Security, Stuart said that:
“As this is now confirmed as being actively scanned and exploited in an automated fashion via botnets, and we know there is the potential for root privilege remote code execution, any open OMI ports must be closed as soon as possible, and Azure mitigation guidelines need to be implemented.”
About the Vulnerabilities
The flaws were identified in the Open Management Infrastructure aka OMI. It is a widely used software component embedded in many popular Azure services. These include a remote code execution vulnerability classified as CVE-2021-38647 and several privilege escalation flaws including:
What are the Dangers?
An attacker can remotely exploit CVE-2021-38647 simply by sending out a well-crafted request to a vulnerable device using a publicly accessible remote management port, such as 5986m 5985, or 1270. If the attack is successful, the attacker can become a root on a remote device.
Furthermore, Azure will automatically install the OMI agent after a user set up Linux VM and other services, including monitoring, are enabled on the device. Then, OMI will run with root access by default, making the system highly vulnerable to compromise.
Security researcher Kevin Beaumont (GossiTheDog) tweeted that if Mirai botnet exploits a vulnerable machine, the operators will drop one of the Mirai DDoS botnet versions and close port 5896 on the internet to prevent other attackers from exploiting the same box.
“Mirai botnet is exploiting #OMIGOD—they drop a version of Mirai DDoS botnet and then close 5896 (OMI SSL port) from the internet to stop other people exploiting the same box,” Beaumont’s tweet read.
SEE: Whitehat hackers accessed primary keys of Azure’s Cosmos DB customers
According to Beaumont, one of his test boxes was attacked, and attackers deployed a cryptominer on the system.
For anybody who hasn’t caught the #OMIGOD patching thing.. Azure haven’t patched it for customers.
They silently rolled out an agent allowed no authentication remote code execution as root, and then the fix is buried in the random CVE – alter your system config. pic.twitter.com/BLjmhQFDg2
— Kevin Beaumont (@GossiTheDog) September 16, 2021
For your information, Mirai is a destructive botnet, for example, in 2019, it was reported that a British man used Mirai botnet to cripple the Internet services in the Republic of Liberia, a country on the West African coast.