Last August, a Malware called Mirai was discovered. Now, it appears that it has a new variant that has launched a 54-hour DDoS-attack against an unnamed US college.
According to Imperva Incapsula, the attack occurred a month ago on February 28, and yet it is only now that the news it out. Researchers believe it to be a new variant of Mirai that is “more adept at launching application layer assaults.”
More: what is Mirai botnet, what it has done, and how to find out if you’re part of it
During the attack, the average traffic flow measured was 30,000 RPS (Requests Per Second), and the highest peak was at 37,000 RPS. The DDoS mitigation firm said that it was the most they have seen out of any Mirai variant so far. They reported that the attack generated more than 2.8 billion requests.
The attack lasted for 54 hours and was in a league of its own since most of the application layer assaults lasted under six hours.
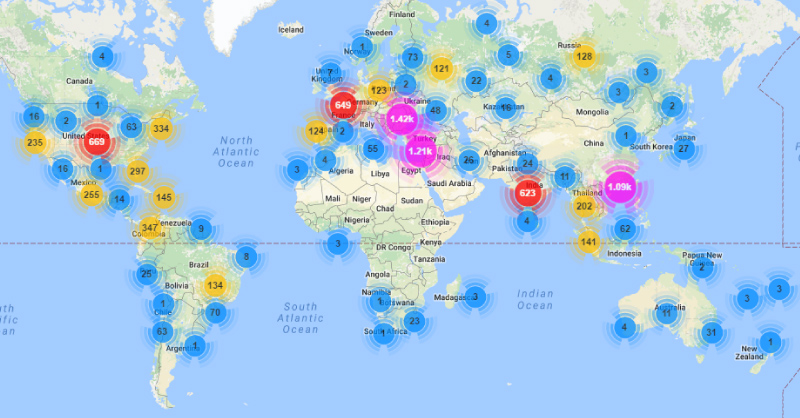
Researchers also observed a pool of attacking Internet of Things (IoT) devices usually associated with Mirai, such as DVRs, routers, and CCTV cameras. It has been discovered that the attack traffic originated from 9,793 IPs from all over the world, but 70% of the botnet traffic originated in 10 countries.
Most of the traffic was found to be originating from the US, with 18.4 percent of the IPs leading somewhere inside the US borders. Next in line by the IP botnet percents is Israel with 11.3 percent, Taiwan with 10.8 percent, India with 8.7 percent, Turkey with 6 percent, Russia with 3.8 percent, Italy, and Mexico both have around 3.2 percent. Finally, there is Colombia with 3, and Bulgaria with only 2.2 percent of botnet traffic.
More: This IoT Scanner Shows if Your Device can be used in a DDoS Attack
More Mirai signature factors helped researchers to identify the attack, such as header order and header values. However, what finally lead the form to believe it’s a new version of Mirai is the number of different user-agents. Apparently, the DDoS bots hide behind different user-agents than the five known to be a part of the default Mirai version. This time, it used 30 user-agent variants. Incapsula said that this means the new variant was modified to launch more elaborate application layer attacks.
A day after the 54-hour-attack ended, another one was launched, but this time it only lasted an hour and a half. This time, the average traffic flow was only 15,000 RPS.
Remember, Mirai malware was first used during a massive DDoS attack on DYN DNS leading to a complete shutdown of Twitter, PayPal, and several other websites for several hours. The same malware was then used in 1 Tbps DDoS attack on France-based OVH hosting; the attack was labeled as the largest DDoS attack in the history.