Mac devices are known for their security, but things are changing now since hackers and cyber-criminals are coming up with new ways to target Mac users. Recently, the IT security researchers at Fortinet discovered a ransomware campaign that uniquely targets Mac OS and is being offered as a ransomware-as-a-service (RaaS) on dark web. Although this is not the first instance of RaaS, it is, however, still troubling as it can shift the focus from Windows to the seemingly safe Mac devices.
[irp posts=”51040″ name=”Hackers Selling Undetectable Proton Malware for macOS in 40 BTC”]
RaaS for Macs
Dubbed as MacRansom, this Mac ransomware malware is not all that harmful in its operation. Nevertheless, it is still a subject of concern as it can lock a victim’s files and demand ransom and threaten users by stating that all their files will be deleted within a week if the payment is not made.
The service is offered to newbies as well which means that it is safe to predict that after Windows, Macs will now become the focal point of mainstream ransomware.
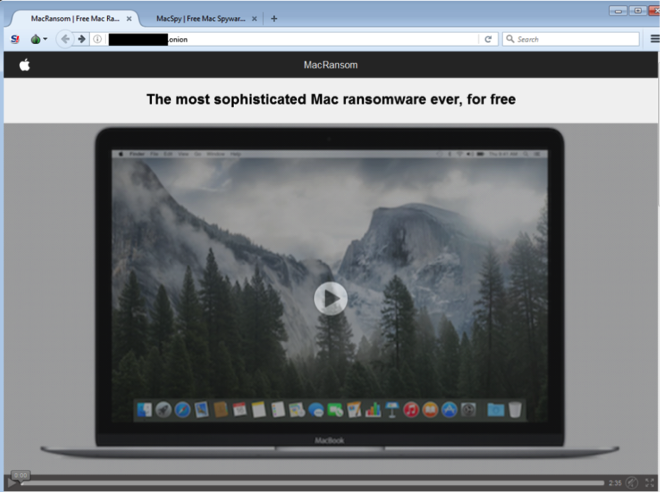
Screenshot from the Dark Web marketplace where the ransomware malware is being sold.
How does it work?
According to the researchers, the ransomware comes with a trigger that is set as per demanded by the buyer. The trigger is associated with a time switch that activates once the trigger gets active.
It is only after the trigger is activated that files start to get encrypted in a victim’s system. This means that the ransomware does not start encrypting files as soon as it enters the system. Rather, the attack is delayed.
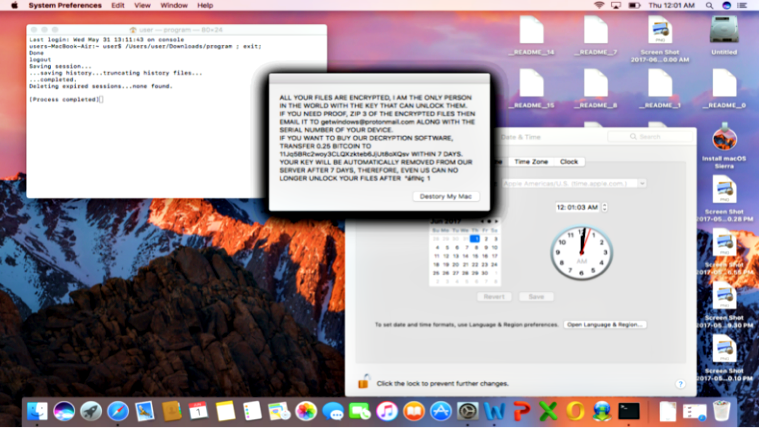
Nevertheless, researchers say that only 128 files can get encrypted and therefore the virus is not as harmful as others, albeit, it is still able to alter the Time Date Stamp, implying that no recovery tools will serve a useful purpose.
The ransom demanded amounts to 0.25 bitcoins which are equivalent to $700, and victims need to email the perpetrator if they are to pay the amount and have their files unlocked.
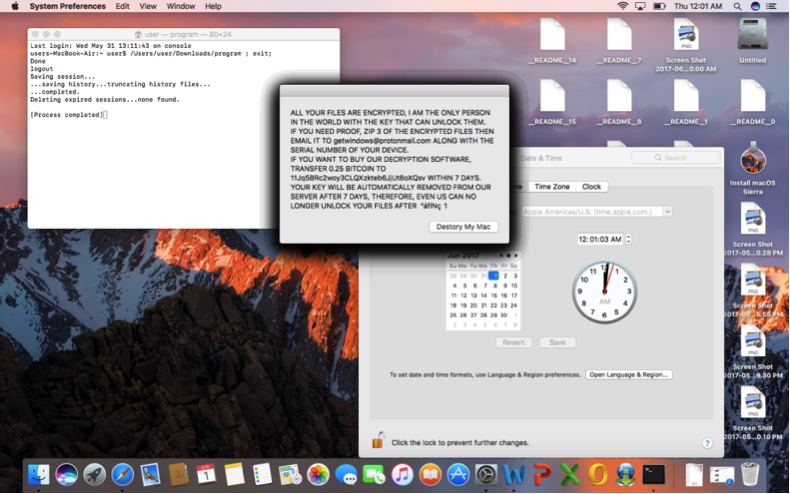
Ransome Note
According to Rommel Joven and Wayne Chin Yick Low of Fortinet:
“It is not every day that we see new ransomware specifically targeting Mac OS platform. Even if it is far inferior from most current ransomware targeting Windows, it doesn’t fail to encrypt victim’s files or prevent access to important files, thereby causing real damage.”
“Last but not the least, this MacRansom variant is potentially being brewed by copycats as we saw quite a lot of similar code and ideas taken from previous OSX ransomware. Even though it utilizes anti-analysis tricks, which differs from previous OSX ransomware, these are well-known techniques widely deployed by many malware authors. MacRansom is yet another example of the prevalence of the ransomware threat, regardless of the OS platform being run. There are no perfect mitigations against ransomware. However, the impact can be minimized by doing regular backups of important files and being cautious when opening files from unidentified sources or developers.”
[irp posts=”53226″ name=”Snake Malware Modified; OS X The Next Target”]
The threat can spread
Researchers worry since a Mac ransomware has now emerged in cyberspace, it is only a matter of time before other spammers and hackers develop a copy which can be much more sophisticated in terms of damage caused than MacRansom.
Furthermore, it has been revealed that the developers of MacRansom have other offerings, one of which is the MacSpy malware which was discovered by AlienVault.
The malware is similar to MacRansom and has features which allow attackers to use key logs and obtain files that are synced with iCloud. There is a paid version as well which contains more advanced functionalities.
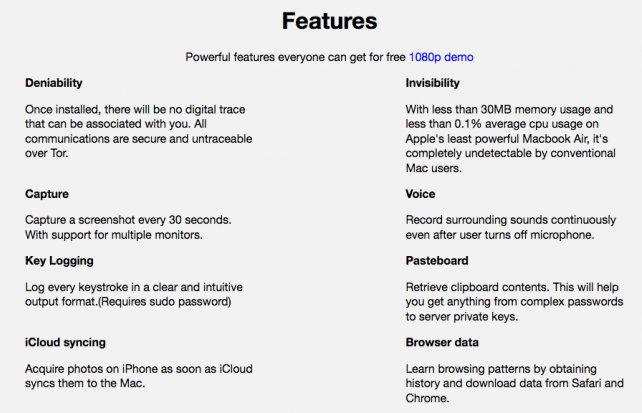
MacSpy’s features (Image Credit: AlienVault)
Macs not so safe after all
Given that it was mostly Windows that became the target of ruthless ransomware attacks, it is surprising to see that Macs have now been taken into the fold as well. Perhaps this is due to the fact that Mac users have grown in the past years.
[irp posts=”51212″ name=”10 Powerful But Not Yet Promoted Antivirus for PC, Mac, Android, iPhone”]
DDoS attacks are increasing, calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.