Having a high-profile and so very sought-after device like Nintendo Switch is a risky deal as cyber-criminals are always on the hunt of salient vulnerabilities in these devices to fulfill their malicious goals. No matter how strong the defenses of these high-end devices may be, hackers would find a way to bypass them. Same has happened in the case of Nintendo Switch.
Only a week has passed since the launch of Nintendo Switch, and the famous iOS jailbreaker qwertyoruiop has already discovered a way to exploit it. It is worth noting that qwertyoruiop is the same hacker who played a vital role in the infamous PS4 1.76 jailbreak. In fact, he is known for jailbreaking some iOS versions. But in this case, qwertyoruiop claims he did not jailbreak the Switch.
Just to be clear: I did not jailbreak the Switch. I simply demonstrated a proof of concept exploit that gives me code exec in the browser.
— qwertyoruiop (@qwertyoruiopz) March 13, 2017
More: Android-compatible Google Daydream VR Controller Hacked to Run on iOS
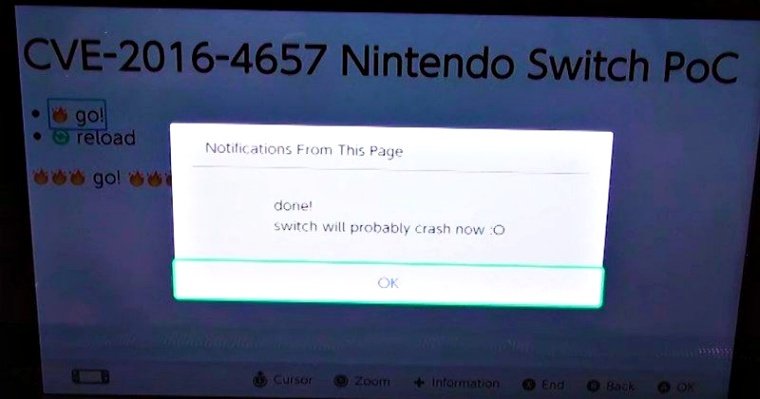
Qwertyoruiop has proved that he was able to hack Nintendo Switch through his tweet that contained an image of the hacked Switch device. Developer LiveOverflow has also confirmed that an iOS 9.3 WebKit exploit (CVE-2016-4657) is effective on Switch. He also has published a proof of concept to prove his point, which confirms that the browser in Switch is vulnerable to hack attacks.
So what is the connection between the WebKit and Switch?
There is a strong connection; although Switch doesn’t have its web browser it does have a web browser that is required for performing captive portal logins to enable internet connectivity at any public spot like a parking lot or café hotspot. This is why Switch has Apple’s WebKit engine. It is an open source engine that works on Mac and iOS through Safari.
[fullsquaread][/fullsquaread]
The Switch uses a version that is pretty out-dated as it came with iOS 9.3 and this version contains a vulnerability that lets Pegasus malware infect the iPhone. This vulnerability was patched in iOS 9.3.5, but surprisingly Nintendo preferred to use the older version and expected that no one would notice. But, qwertyoruiop already has ample experience in playing with iOS 9.3 WebKit browser and therefore, he was able to utilize the old exploit where he stripped off the iOS code and made it work on Switch.
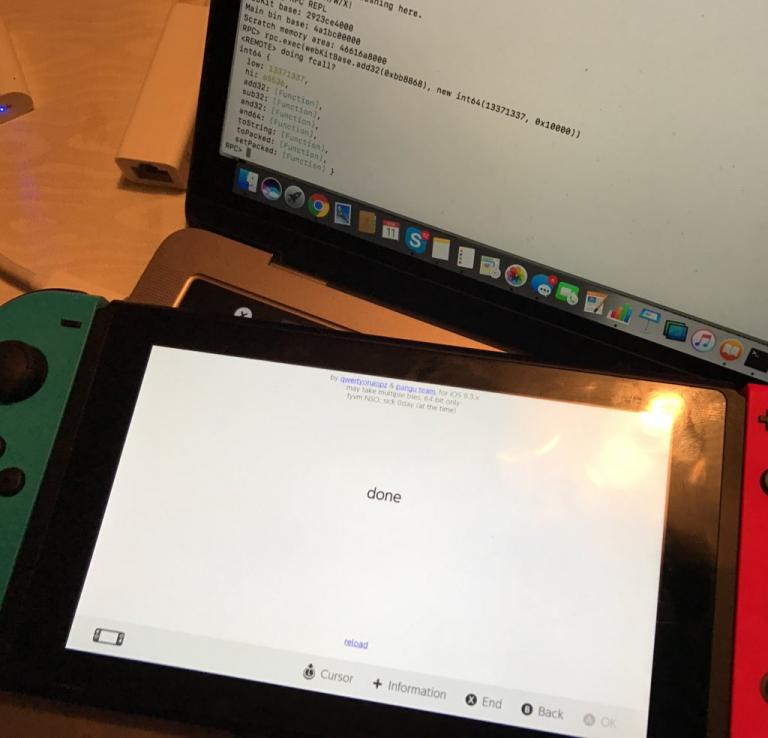
LiveOverflow’s proof of concept video shows the process in detail and also provides an explanation of how this exploit works.
[fullsquaread][/fullsquaread]
More: Researchers Send Secure Passwords Using the Human Body
For the hacking fraternity, this revelation is like a breath of fresh air as it provides them an open opportunity to further analyze Nintendo Switch OS, explore its memory and get an in-depth understanding of the firmware. However, there is a long way to go to attain complete control on Switch’s functions, but at least they have a starting point in hand.
On the other hand, it is the perfect time for Nintendo to release a firmware update so that the issue could be rectified.
VIA: Wololo.net
DDoS attacks are increasing, calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.