An unknown hacking group has been targeting organizations in North Korea with Konni Malware. It is a RAT/remote access Trojan having all those features that any effective backdoor might have such as host profiling and remote access control. In 2017, already three different campaigns were identified by security experts against North Korean companies using this malware.
Talos Intelligence, a cybersecurity firm owned by Cisco, firstly identified the campaign in which Konni malware was used. This campaign was launched against North Korea on July 6th, just a few days after the testing of the missile. Talos stated that the campaign most likely was related to the “launch and the ensuing discussion of North Korean missile technology.” In total, Talos identified two campaigns using Konni.
On the other hand, a similar campaign was noted by Cylance security firm’s researchers on Tuesday. This strengthened the findings of Talos and further established the notion that North Korea was being targeted with Konni.
The latest Konni campaign uses a Word document containing the content of a news article published by a Korean news agency Yonhap. This document is infected with a malicious executable file the purpose of which is to invade the computer where it is opened. As soon as this file is executed, the malware starts communication with its C&C server for further instructions and to fulfill the attacker’s malicious objectives.
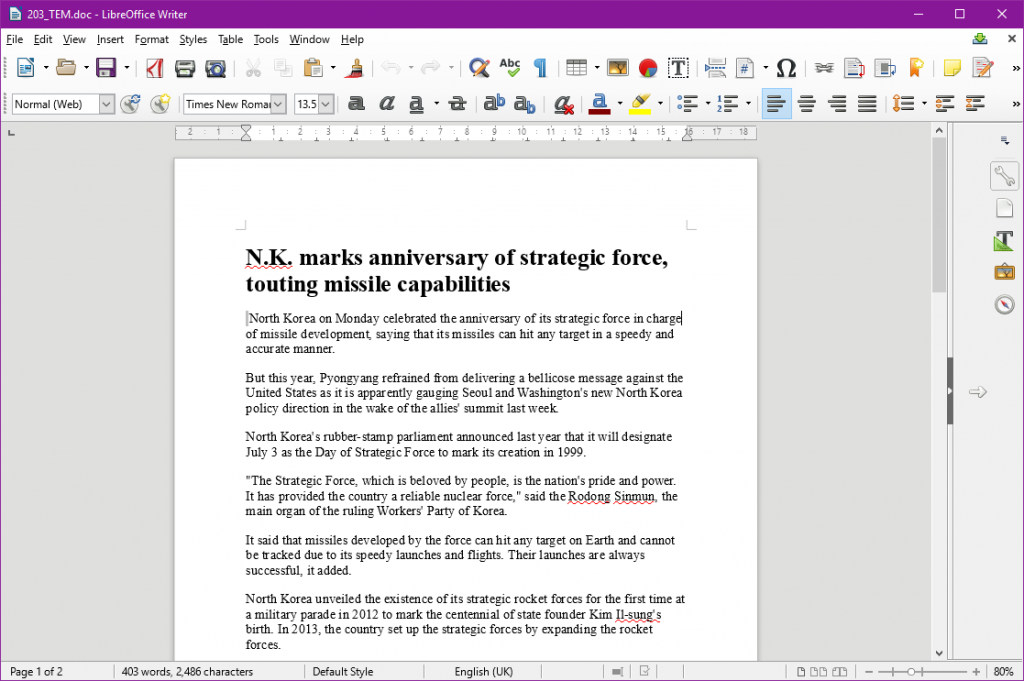
Image Credit: Talos Intelligence
Cylance’s security experts state that these campaigns were noticed in July. The reason behind the latest surge in malware campaigns against North Korean organizations is yet unclear, and experts believe that the campaigns seem to be espionage efforts by those who are “interested in North Korean affairs.”
Konni malware is capable of hiding in the background while the victims are tricked in such a way that they end up executing its payload. The malware also has screen capturing and keylogging capabilities due to which it manages to steal data from targeted computers.
Apart from Konni, there is another malware targeting North Korean firms. BitDefender identified that a new campaign is also active where an enhanced version of DarkHotel malware is used dubbed as Inexsmar. Just like DarkHotel, which targeted business execs and prominent figures visiting hotels, Inexsmar targets political personalities.
The campaign using Inexsmar was identified in July, and it delivers a malicious payload to the target instead of exploiting the zero-day vulnerability as is the usual norm. Inexsmar campaign contained a malware dropper called Pyongyang Directory Group email SEPTEMBER 2016 RC_OFFICE_Coordination_Associatewxcod.scr.”
This dropper is identical to the document used in the Konni campaign, aptly titled “Pyongyang Directory Group email April 2017 RC_Office_Coordination_Associate.scr.” Furthermore, the files used in Konni and Inexsmar campaigns both include a similar set of names and contact information, which belonged to North Korean embassies, United Nations and UNICEF.
Cylance researchers state that the attacks leveraging intelligence gathering and social engineering skills are extremely devastating for the targeted companies because these “target user’s (very human) emotions of trust, and can lead to a total take over.”
Previously researchers from Kaspersky Lab claimed that the hackers behind Konni malware campaigns might be of Korean origin and the campaigns are probably originating from South Korea. This comes as no surprise because espionage attacks are quite common between South and North Korea.
Security researchers believe that the attacks could also be retribution campaign since the country recently tested an intercontinental ballistic missile (ICBM) successfully.









