A quick Google search for the “most secure messaging apps” introduces you to “Signal – a private messenger.” Yet, who knew that it still would be vulnerable?
On Saturday, September 29, Google’s Project Zero team which is responsible for finding previously unknown exploits discovered that calls on the app could be answered even if the receiver did not authorize any such connection. In simple words, calls could be picked up without your knowledge.
This little eavesdropping process happened to be possible because of a method named “handleCallConnected” in their Android client. Used normally when one needs to accept an incoming call and at the same time when the caller is notified that the call has been accepted using a “connect message”.
However, with the help of a modified client, the connect message can be sent when the user has not accepted the incoming call himself resulting in the connection being made. As for the iOS client, it also had the same problem but luckily a UI error interrupted the process and didn’t let such a connection be made.
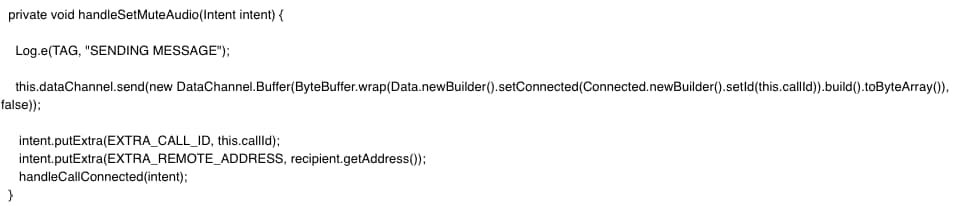
As for how attackers could have or do exploit this neat technique is no mystery. The Project Zero Team has in fact laid down the entire process one needs to initiate in order to do so. Firstly a modified client needs to be created where the ” handleSetMuteAudio” method is replaced with the following method in a file named WebRtcCallService.java:
Once this is done, the attacker needs to make a call to the user, wait for it to ring and press the mute audio button from their own phone. This will automatically make the user’s device answer the call resulting in a successful eavesdropping attack.
It is worth noting that in the entire process, the user would effectively-know once the call was connected for real as explained by the app’s co-founder Moxie on Twitter:
Thanks to Natalie for finding this!
Worth noting that it was Android only, your phone would ring, display as a connected call, and log the completed call at the top of your conversation list. It’s not silently “enabling the microphone.” Also fixed.
— Moxie Marlinspike (@moxie) October 4, 2019
Moreover, this vulnerability did not allow video calls to be made in this way. Currently, Signal has patched the exploit by releasing an update for its Android app with version 4.47.7 on the very same day. The team responded fastly and with responsibility which increases consumer trust.
As for a company that monetizes its security concept being found vulnerable, it is imperative to realize that even multi-billion dollar companies suffer from such exploits from time to time as these are inevitable in the cyber-security industry.