Alert: The previously discussed Steam Stealer malware is way bigger than we thought — The malwarE is also embedded with a remote administration tool (RAT)
A couple of weeks ago we warned you about Steam Stealer malware. Now, the latest Steam scam has been discovered with the help of a gamer Patrizza Vampizza’s post on the Activity Feed of the gaming platform, in which she informed her friends about the presence of a suspected bot account. Vampizza is a member of a very popular group on Steam called “Pressure” Skin. The group comprises of thousands of members and like Vampizza, various other members have received the same message. The only difference is that the message has been sent from different private accounts.
The screenshot of the message posted by Vampizza is as follows:
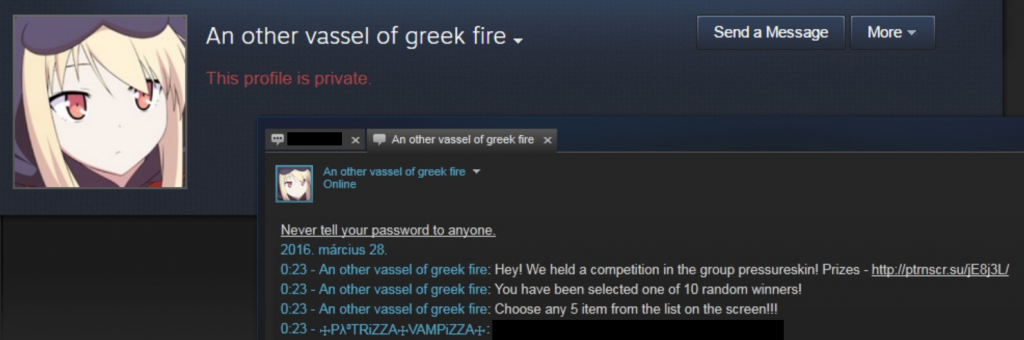
There is every possibility that these are bots but at the same time, it is also possible that these messages are being sent from compromised accounts, which malicious actors are using to spread infected link via Steam chat.
The modus operandi of scammers entails that when the malicious URL link that is present in the spam message ptrnscr[DOT]su/jE8j3L/ is clicked by the users they are instantly taken to the page and a file is downloaded automatically from the Box file-sharing website account. The file is titled Screenshot_3.scr (MD5 FCA73DC665FF51022A7291B76B554809).
This is how the .src file appears on desktops:
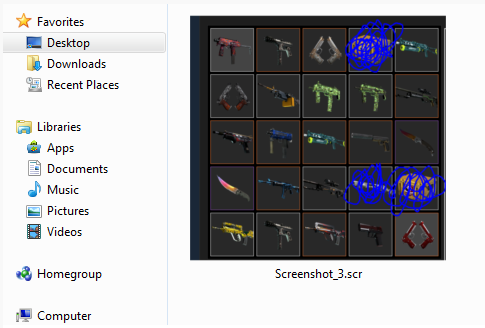
After execution, the victims generally don’t suspect anything unusual on their desktops because the entire activity occurs in the background. The Screenshot_3.scr will start reading information about the system and/or will download other malicious files, or it will prevent the system from identifying them and prompt messages as these will cause errors. It might also link the computer to a Russia-based IP address through a port that is usually associated with the DarkComet RAT. However, the Screenshot_3.scr is a NanoCore RAT. More information on this file can be obtained from this Hybrid Analysis Page.
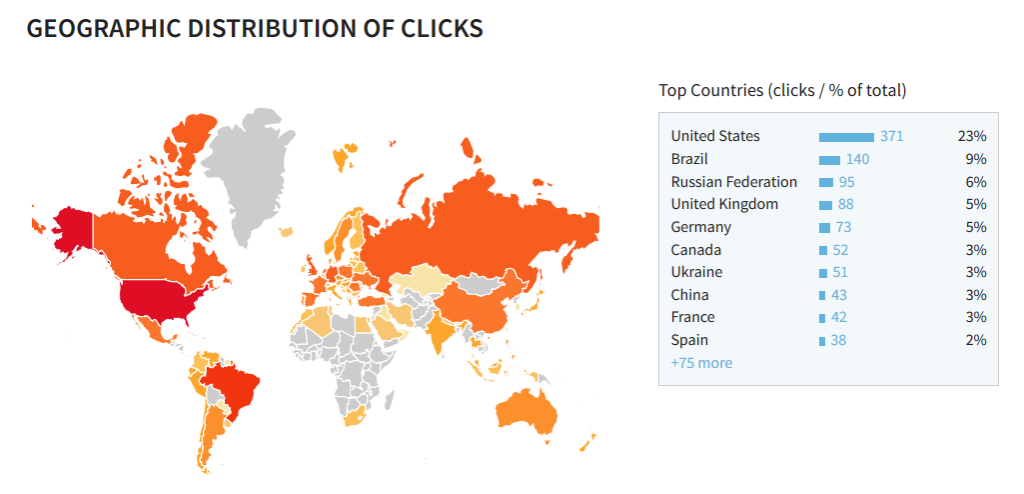
Now, this isn’t a groundbreaking or novel tactic to spread malware at all but we have to admit this is a relatively new technique for most users. Steam malware distribution through chat is a down-to-death tactic, and is often featured by us but still, users continue to get deceived and trapped by scammers. Until now, over 1,500 users have clicked the link ptrnscr[DOT]su/jE8j3L/ believing that a Steam member has sent it to them. Want to check out the geographical statistics of users who have fallen prey to this tactic so far. Check the chart:
The malicious .scr file is detected by Malwarebytes Anti-Malware and users are also secured from accessing the download site. However, we suggest that you never click on links sent to you through some kind of a contest or are part of a package deal. Do check the legitimacy of the source prior to clicking on the link. Also, the Steam community must try to keep an eye on suspicious accounts and immediately report them to Steam or inform friends about it. In case you have become a victim of the attack, we advise you to change your password and spread the word about the experience to spare others from the nightmare.
During recent years, scores of people have faced hacking issues with their Steam accounts. It has almost become a convention that no Steam account is safe enough and the chances of being hacked are always there. Before introducing new security settings, an average of 70,000+ Steam accounts got hacked per month.








