According to researchers, “This is the worst cloud vulnerability you can imagine.”
A critical security vulnerability present in Microsoft’s Azure cloud computing database left the sensitive data of thousands of customers exposed. These customers included several Fortune 500 companies.
The vulnerability existed in Microsoft Azure’s flagship database service Cosmos DB for approximately two years. The good news is that the vulnerability was only exploited by a team of researchers at Wiz which is a Palo Alto, California-based cyber security company that helped identify this issue in the first place.
SEE: 21m login credentials of Fortune 500 companies found on dark web
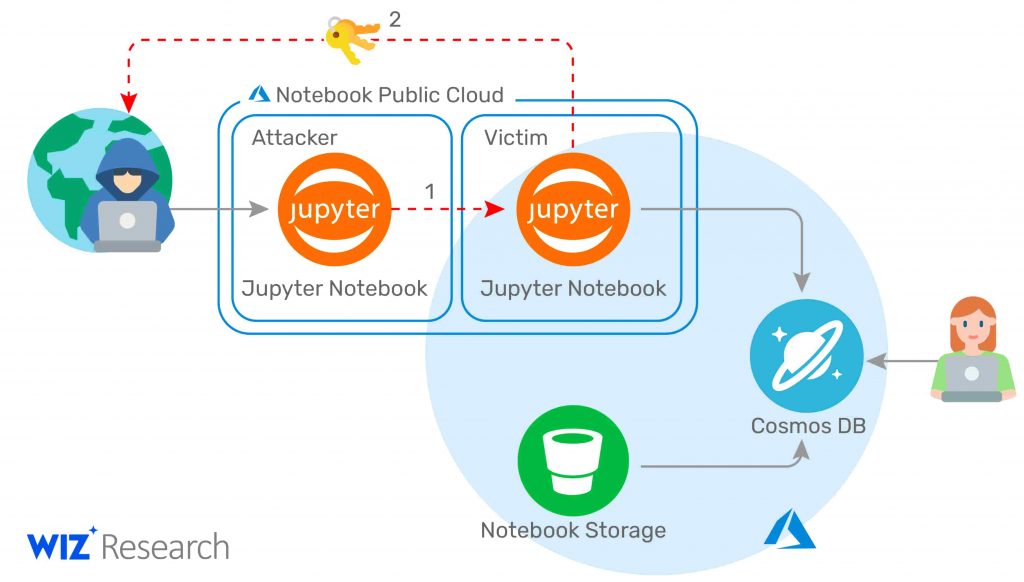
The flaw affected the data visualization feature knows as Jupyter Notebook. Azure added this feature to Cosmos DB in 2019. Its purpose is to help users create customized views of their data. In February 2021, Microsoft turned on this feature by default for every Azure customer.
According to Wiz’s blog post, if left undiscovered, data of approximately 3,300 Azure users would have been exposed to attackers. These customers included companies like:
- Coca-Cola
- Walgreens
- ExxonMobil
- Schneider Electric
- Liberty Mutual Insurance and other high-profile clients.
Ami Luttwak, the Chief Technology Officer at Wiz commented on the issue and emphasized that:
“This is the worst cloud vulnerability you can imagine.” […] “This is the central database of Azure, and we were able to get access to any customer database that we wanted.”
Fortunately, there was no attack on the database through this vulnerability which is why customers’ data remained secure. Microsoft has also confirmed that there are no signs of any malicious activity on their database.
In an email to Bloomberg, the tech giant said that:
“There is no evidence of this technique being exploited by malicious actors, we are not aware of any customer data being accessed because of this vulnerability.”
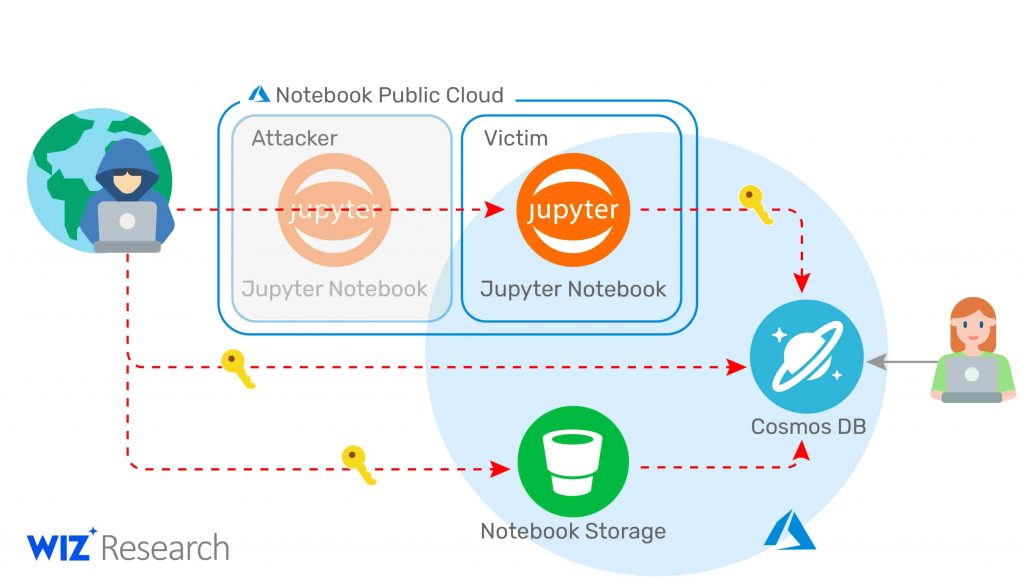
On the other hand, Wiz researchers highlighted the severity of the vulnerability by revealing that they were able to get access to the primary keys of Cosmos DB customers. These primary keys can enable anyone to get full read, write, or delete access to all the data present in Cosmos DB.
Microsoft fixed the vulnerability two days after the report came in from Wiz. Additionally, to make the system secure, Microsoft has advised all the customers to change their primary keys as they do not have the access to update them.
Hackread.com can confirm that Microsoft paid a sum of $40,000 to researchers as part of its responsible disclosure and bug bounty program.
Nevertheless, companies around the world are increasingly moving to and depending on cloud storage. This makes cloud infrastructure a lucrative target for threat actors.
Remember, in January 2021, the US Cybersecurity and Infrastructure Security Agency (CISA) also issued a warning to alert companies using cloud storage about a possible security breach when one of the companies had their account breached even though they were using “proper multi-factor authentication (MFA).”