Cybersecurity specialists report detecting a new wave of attacks potentially linked to the Avaddon ransomware variant. This is a strain detected in early 2019 and is advertised as an as a service (RaaS) ransomware platform.
Recently a joint investigation by security firms in the United States and Australia detailed this new wave of attacks, detected in dozens of countries and impacting all kinds of public and private organizations.
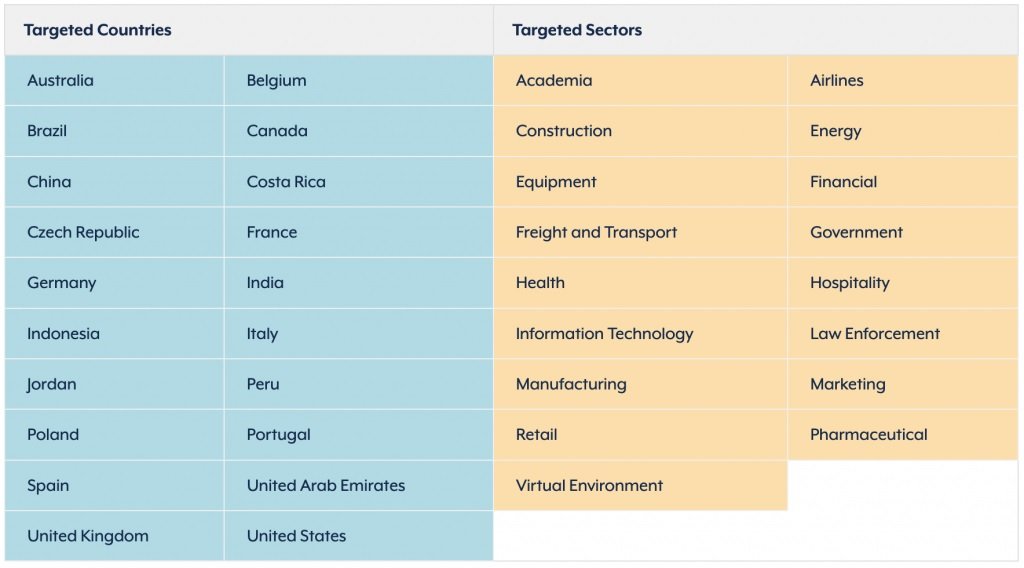
Moreover, the Federal Bureau of Investigation (FBI) notes that the efforts of its specialized units to combat these practices have increased: “Threat actors behind Avaddon compromise affected systems through compromised login credentials to access remote desktop systems or VPN services,” the report states.
Avaddon infections also involve the scheme identified as “double extortion,” in which threat actors also steal sensitive information to filter it on hacking platforms, forcing victims to negotiate a ransom. This leaking comes in 3 steps defined by the FBI researchers:
- Warning: After gaining access to a target network, hackers leave a ransom note on the victim’s network and issue a warning about the potential leak of sensitive information
- Initial leak: If the affected organization does not pay the ransom within a certain timeframe, hackers begin to press by leaking a share of the compromised information on dark web
- Full Leak: If the ransom is not paid after the set deadline (usually a week), hackers end up publishing all compromised information, which is available to any group of threat actors
Avaddon developers also claim that they have the ability to perform denial of service (DoS) attacks, although the FBI investigation specifies that no DoS attack incidents linked to this hacking group have been detected.
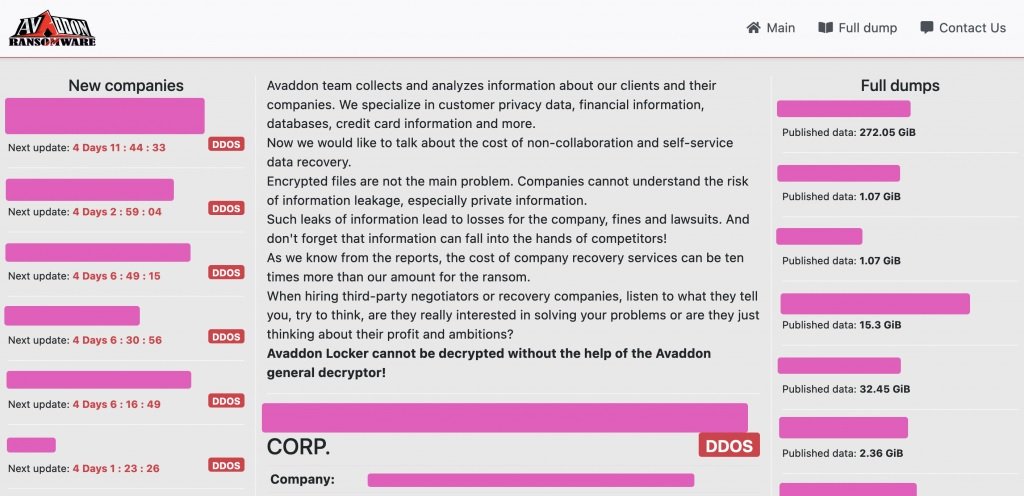
According to data collected by the ID-Ransomware platform, approximately 20 Avaddon attacks are reported per week, although at the moment there is no official data on the number of attacks that ends in the payment of a ransom or in the negotiation stage.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.