The cybersecurity researcher working for ThreatFabric made the discovery, and the company issued a warning, about a new and more sophisticated kind of voice phishing known as vishing. In recent years, the prevalence of Vishing, which is also known as Voice over IP Phishing, has increased to the point that it has undermined people’s faith in calls coming from numbers they are unfamiliar with.
Even though it would be upsetting to get phone calls from people professing to work at the bank, the likelihood that every incoming call you get throughout the day is coming from a con artist is incredibly high. During the course of their routine investigations into potential dangers, they came across a previously unknown collection of malicious programs that were quite similar to those that Kaspersky had identified.
“Letscall” is the name given to this toolset by the threat actor group that is responsible for these campaigns. At the moment, the victims of these campaigns are people living in South Korea. In a purely technical sense, there is nothing stopping them from expanding the scope of the assault to include nations inside the European Union. In other words, we are dealing with a framework that is completely functional and ready to be utilized. This framework has all of the instructions and tools necessary to run the afflicted devices and to connect with the victims. It is possible for any threat actor to use this framework.
Most likely included in this group are:
- Android developers who are conversant with the contemporary notion of VOIP traffic routing. They refer to participants in one of the phases as “developers” since they noticed command name discrepancies throughout that stage.
- Designers who are accountable for the web pages, iconography, and content of the administrative panel, phishing web sites, and mobile harmful apps they create.
Frontend developers that are proficient in JavaScript programming and have experience with the processing of VOIP communications. - Backend developers that are experienced with the methods used to safeguard the backend API against unauthorized access.
- Call operators who are proficient in a variety of languages and have experience in conducting voice-based social engineering attacks.
The attack is divided into three phases, which are as follows:
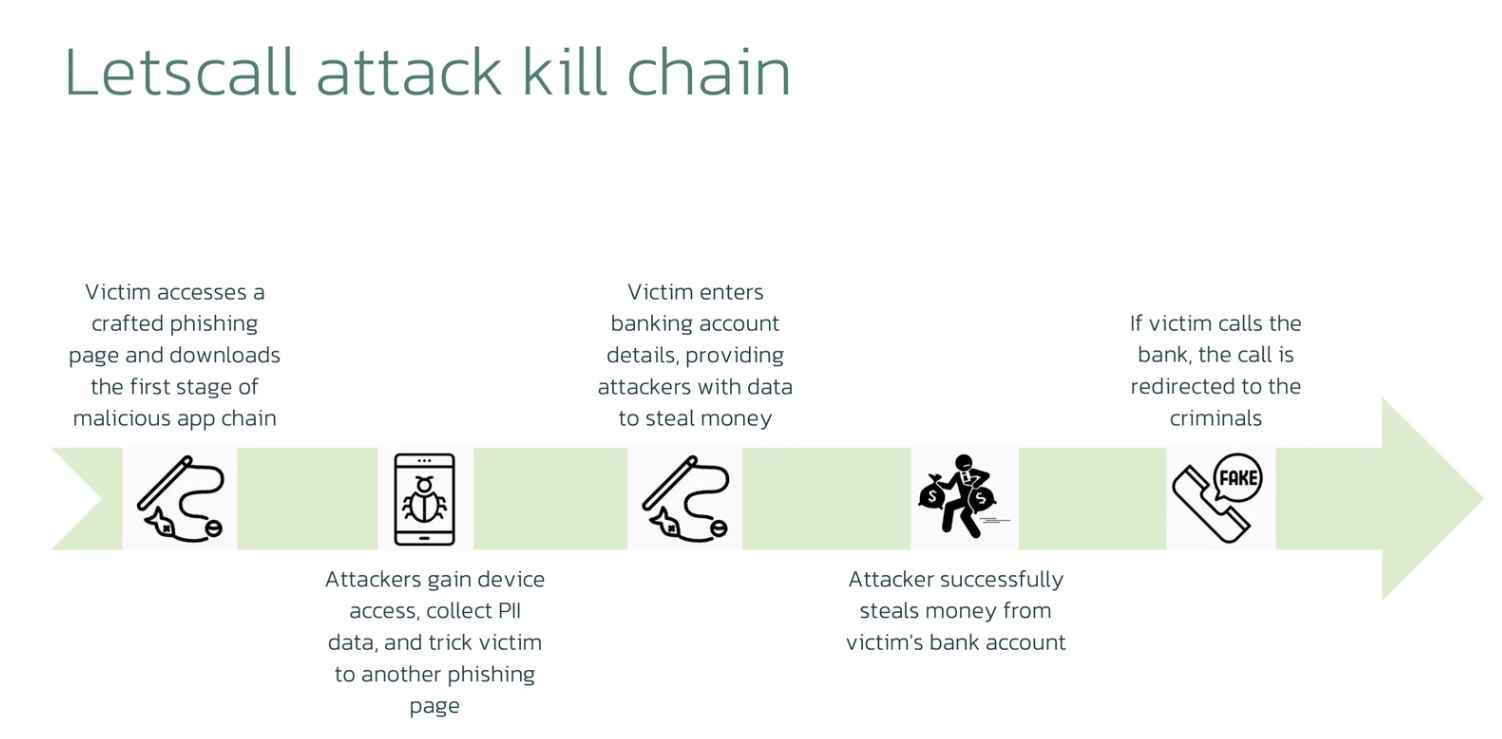
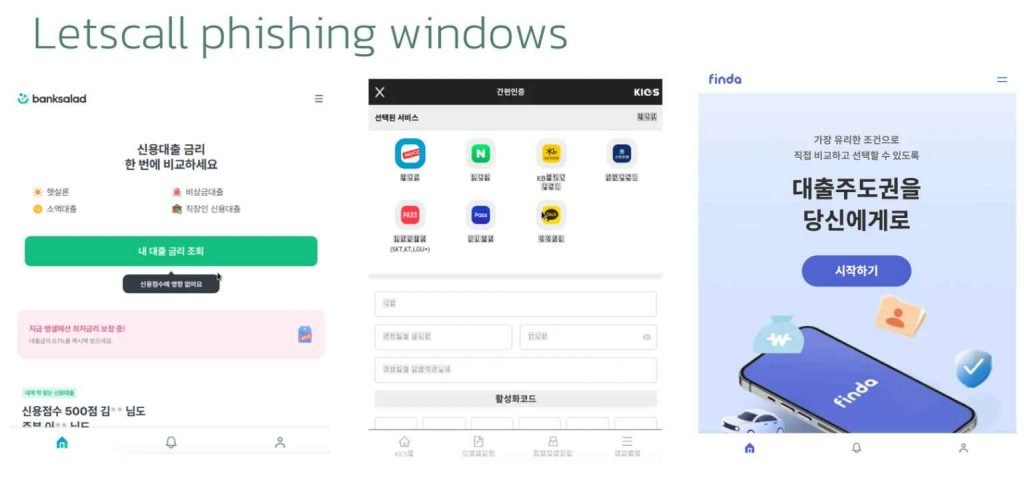
Phishing takes place when a victim accesses a website that has been designed to seem to be the Google Play Store. The first malicious program in the chain is downloaded by the victim from that URL, which is the first step in the chain.
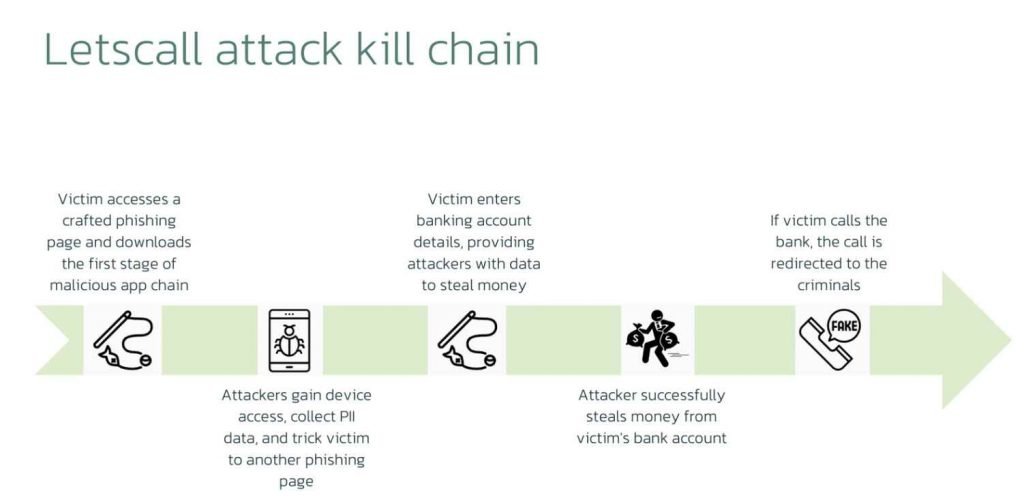
This first step, which we will refer to as the downloader, will access the phishing web page, execute preparations on the device, gain the appropriate rights, and install the second stage malware, which will be downloaded from the control server.
The second step of the attack is a strong spyware program that the attacker will use to both exfiltrate data and enroll the infected device in a peer-to-peer voice over Internet Protocol (P2P VOIP) network that will be used to connect with the victim through audio or video conversations. Additionally, a third step, the subsequent link in the chain, is removed by this application. Letscall makes advantage of WEBRTC technologies in order to redirect the VOIP traffic and establish a connection between the victim and call-center operators. Letscall employs STUN/TURN technologies, including Google STUN servers, to circumvent network address translation (NAT) and firewalls to obtain the highest possible quality for phone or video calls.
The third stage is a companion program that extends some of the functionalities of the second stage malware. It has phone call capability, which is used to divert the call from the victim device to the contact center that is controlled by the attacker.

After conducting an investigation into the “Letscall” malware operations, they discovered a cybercriminal organization that is well-versed in Android security as well as contemporary voice routing technology. The researchers demonstrated that social engineering assaults that are technically sound but poorly executed may nevertheless pose a significant risk.
It is evident that technical features are just as vital as social engineering, which is supported by the care the group devotes to creating phony Google Play sites, stolen logos of the existing Korean apps, along with a novel approach employing nanoHTTPD to drop the payload. This is obvious evidence that technical features are just as important as social engineering.
Theft of resident registration numbers (or IDs) may open numerous doors for cybercriminals, and we anticipate this attack vector only increasing as more and more electronic ID solutions are used by governments as well as private businesses and public organizations. It is not uncommon for Asian threat groups to make use of an evasive method that has already been used by other actors. It’s probable that certain software engineers in one location do work for more than one cybercrime organization, even if they aren’t physically located next to one other in the same office building.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.